My name is Cristian, I am a systems and security engineer.
Passionate about the world of computer science and cybersecurity.
I want to share with everything about the world of cybersecurity in a way easier to understand and bring it closer and closer.
Highlights
Servidores de Microsoft Exchange hackeados a través de aplicaciones OAuth para el phishing
Microsoft dice que un actor de la amenaza obtuvo acceso a los…
Métodos de ataque: Command Injection
La inyección de comandos es un ciberataque que implica la ejecución de…
Las actualizaciones del martes de parches de Microsoft provocan errores de autenticación de Windows AD
La actualización del parche de mayo de Microsoft está provocando errores de…
Kerberos Golden and Silver Ticket Attack
Hoy les traigo un tutorial muy sencillo y que mucha gente me…
Cobalt Strike se distribuye en servidores MS-SQL vulnerables
Los servidores Microsoft SQL (MS SQL) vulnerables que se conectan a Internet…
Pentesting Active Directory con Responder
Muchas personas me están preguntando sobre métodos de prevención de ataque del…

Learning to exploit the Linux Kernel – Part 1
In this series, I’m going to write about some basics in Linux kernel exploitation that I’ve learned over the past few weeks: from basic environment configuration to some popular Linux kernel mitigations, and their corresponding exploitation techniques. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the only purpose of learning. We do…
Active Directory Pentesting with Responder
Many people are asking me about Active Directory attack prevention methods and a good way for a critical vulnerability scan, which then leads me to get the domain administrator in fifteen minutes by simply exploiting misconfigurations in AD. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the only purpose of learning. We…
Antivirus, what is it, why do I have to have it?
Nowadays we all know what an antivirus is, we know what we must have to stop a virus from entering our computer and making it unusable. The basic theory is fine, but to really know in depth what an antivirus does? I will explain in depth what it is and the reason for having it.…
SMB What is it and how does it work?
Short for Server Message Block, SMB is an application layer protocol that enables file, printer and device sharing and inter-process communication (IPC) between applications on a network through a client-server architecture. In other words, computers (SMB clients) on a network can connect to SMB servers to access shared files and directories or perform tasks such…
Attack methods: Command Injection
Command injection is a cyberattack that involves the execution of arbitrary commands on a host operating system (OS). Typically, the threat actor injects the commands by exploiting an application vulnerability, such as insufficient input validation. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the only purpose of learning. We do not promote…
CASB, what is it? and main uses
What is a CASB? According to Gartner, a cloud access security broker (CASB) is a security policy enforcement point, either on-premises or in the cloud, located between cloud service consumers and cloud service providers, whose purpose is to combine and enforce corporate security policies when accessing cloud resources. The CASB is like a policeman enforcing the laws…
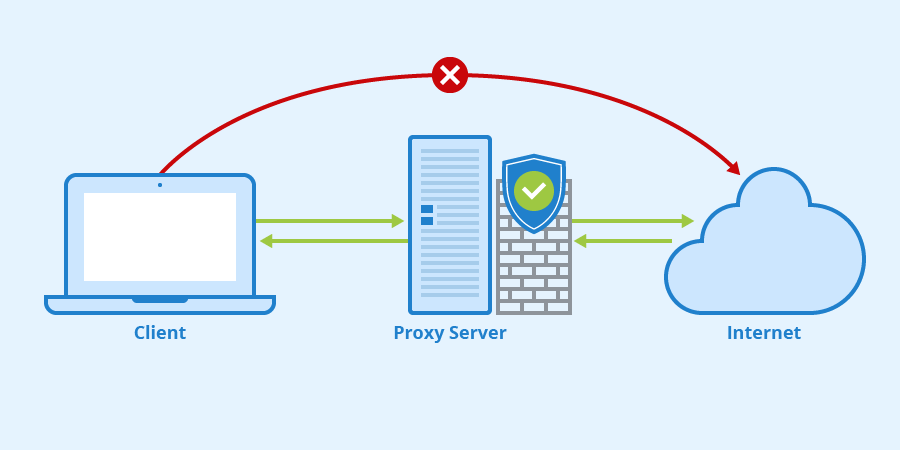
What is a proxy and what is it for?
A proxy is a well-known technology in the market, although sometimes it is not well understood how it works. Therefore, in this opportunity we will explain what a proxy is and how it is useful. But before we start talking about the logical structure of proxy servers, I consider it important to clarify how it…
Attack methods: Code Injection
Code injection is the general term for attack types that consist of injecting code that is then interpreted/executed by the application. This type of attack takes advantage of mismanagement of untrusted data. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the only purpose of learning. We do not promote its use for…
How to configure PROXYCHAINS in KaliLinux via Terminal
Proxychains is an open source software for Linux systems and comes pre-installed with Kali Linux, the tool redirects TCP connections through proxies such as TOR, SOCKS4, SOCKS5, and HTTP (S) and allows us to chain proxy servers. With proxychains, we can hide the IP address of the source traffic and evade IDS and firewalls. Requirements:…
Access Windows 10 without knowing the password
Surely more than one has happened to you that you have forgotten the password of your windows or a Windows 10 that was in domain is not able to access the AD. In this tutorial I will show you how to enter the machine without knowing the password, either physical or virtual machine (in this…
DNSSEC What is it?
One of the cornerstones of the Internet is the Domain Name System, also known by its acronym DNS. The purpose of this protocol is to translate the domain names used by users into IP addresses that can be interpreted by machines. This protocol dates back to the 1980s, a time when functionality prevailed over security, and DNS was…
What is Kerberos, how does it work and what is it used for?
Cybercrime is an unfortunate fact of life today, regardless of whether we are talking about individual consumers or the business world in general. No company or organization is safe, and the problem is not going to get better any time soon. Experts predict that the damage caused by cybercrime will cost the world $6.1 trillion…
Attack methods: Clickjacking
Clickjacking is an attack that tricks the user into clicking on a web page element that is invisible or disguised as another element. This can cause users to unintentionally download malware, visit malicious web pages, provide credentials or sensitive information, transfer money or purchase products online. Requirements: Responsibility: In this tutorial we will use hacking…
Install Linux Subsystem for Windows
The Linux Subsystem for Windows continues to advance in capability and also in ease of use. Earlier this year, Microsoft promised an update to make it and GNU/Linux distributions easier to install, and has just implemented it in the latest Windows 10 Insider Preview Build 20246. Four years ago Microsoft announced a bombshell at its…
How to stop a DDoS attack?
Imagine your website is a store, Distributed Denial of Service (DDoS) is like a mob in front of your store that won’t let your customers in. It’s a nasty situation to have tens of thousands of fake shoppers eating up your valuable resources, all at once. Know how to stop DDoS attacks. DDoS has become…
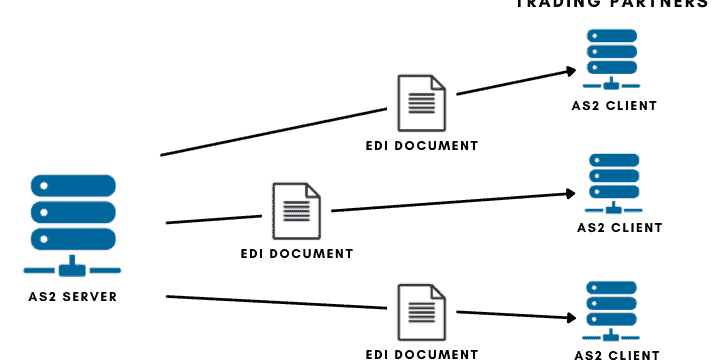
AS2 protocol and differences with SFTP
How are sensitive sectors such as commercial airlines, healthcare or transport communicated and shared data? How do you transfer structured B2B data safely and reliably through risk networks like the Internet? The answer is the AS2 protocol. What is AS2? Applicability Statement 2 ( AS2 ) is a type of file transfer mechanism based on…
Methods of attack: Brute Force Attack
What is the brute force attack method? A brute force attack uses the trial and error method to guess access information, encryption keys, or find a hidden web page. Hackers work through all possible combinations in hopes of guessing correctly. These attacks are carried out by « brute force », which means that they use…
SQL Injection with sqlmap
What is SQLmap? SQLmap is a tool developed in python to automate attacks of the SQL Injection type. Its objective is to detect and take advantage of existing vulnerabilities in web applications. Once one or more possible injections have been detected, the user has the possibility to choose from a variety of options, such as listing…
Permanent backdoor on the remote PC
¿What is the persistent back door? As we know that persistence is also known as permanent. Persistent back doors help us have permanent access to the system. There are many types of persistent rear doors but they work similarly. Usually, the attacker create a backdoor service with the help of metasolpit frame and load in…
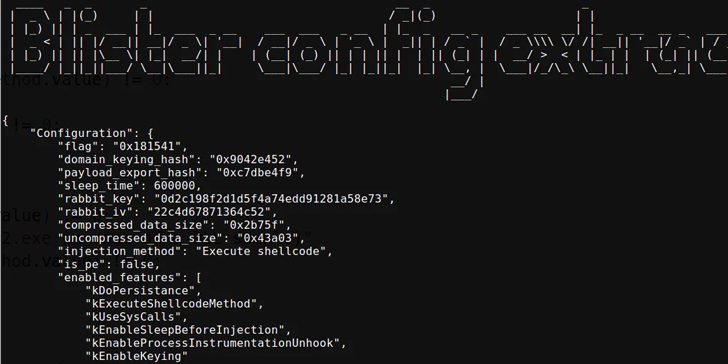
Revisting BLISTER
Preamble In a fast-paced and ever-changing world of cybercrime threats, the tenacity and adaptability of malicious actors is a significant concern. BLISTER, a malware loader initially discovered by Elastic Security Labs in 2021 and associated with financially-motivated intrusions, is a testament to this trend as it continues to develop additional capabilities. Two years after its initial discovery,…
Decrypt user passwords on a Linux system
In this article, we’ll see how to get password hashes from a Linux system and crack the hashes probably using the most widely used password decryption tool, John the Ripper. Requirements: Reposability: In this tutorial we will use hacking techniques, for the sole purpose of learning. We do not promote its use for profit or incorrect…
What is an EDR? Why is it different from an antivirus?
In a world where cyber threats change and evolve at practically the same speed as technology itself, security solutions are needed that not only react to the threat, but are able to anticipate it. Within those proactive solutions we have the EDR system; In this article we explain what it is, how it works and how…
SSH What is it? ¿How does it work?
SSH or Secure Shell, is a remote administration protocol that allows users to control and modify their remote servers over the Internet through an authentication mechanism. Provides a mechanism to authenticate a remote user, transfer entries from the client to the host, and retransmit the output back to the client. The service was created as…
Email Phishing Using Kali Linux
No matter how often you connect and how or why you mainly use the Internet, you have probably seen phishing attack attempts. They are now so common and problematic that cybersecurity professionals regularly provide information to help people detect and avoid phishing attacks. Requirements: Reposability: In this tutorial we will use hacking techniques, for the…
Attack methods: Cache Poisoning
Imagine that, as a high school senior prank, the high school students change all the room numbers in the high school facilities, so that new students who don’t know the high school floor plan yet will spend the next day lost and going to the wrong classes. Now imagine that mismatched room numbers get recorded in…
Top 10 Cybersecurity Trends for 2023: From Zero Trust to Cyber Insurance
As technology advances, cyberattacks are becoming more sophisticated. With the increasing use of technology in our daily lives, cybercrime is on the rise, as evidenced by the fact that cyberattacks caused 92% of all data breaches in the first quarter of 2022. Staying current with cybersecurity trends and laws is crucial to combat these threats, which can…