Imagine that, as a high school senior prank, the high school students change all the room numbers in the high school facilities, so that new students who don’t know the high school floor plan yet will spend the next day lost and going to the wrong classes. Now imagine that mismatched room numbers get recorded in the campus directory, and students keep going to the wrong rooms, until someone notices and makes corrections to the directory.
Requirements:
- Domain – A domain for testing
- Programming – Very high knowledge of programming
Responsibility:
In this tutorial we will use hacking techniques, with the sole purpose of learning. We do not promote its use or for profit or improper purposes. We are not responsible for any damage or impairment that may be generated in the systems used. The sole responsibility of the user of this tutorial.
Knowledge :
- Linux – High
- Programming – Medium
- Kali Linux – Bass
- Windows – Low
- Networks – Very High
Overall Tutorial Level: High
Ideal for: Network engineers, Security engineers, Pentesters
What is DNS cache poisoning?
DNS cache poisoning is putting false information into a DNS cache, so that DNS queries return the wrong answer, and users are directed to the wrong websites. DNS cache poisoning is also known as “DNS spoofing.” IP addresses are the “room numbers” of the Internet and enable traffic to get to the right places. The DNS resolver caches are the “premise directory”. When they cache bad information, traffic is directed to the wrong sites, until the cached information is corrected . (Note that this does not actually disconnect websites from their actual IP addresses.)
Because DNS resolvers typically have no way to verify the data in their caches, incorrect DNS information will remain in the cache until the time to live (TTL) expires or is manually removed. There are several vulnerabilities that make DNS poisoning possible, but the main problem is that DNS was built for a much smaller Internet and was based on a principle of trust (similar to BGP ). A more secure DNS protocol, called DNSSEC , is intended to solve some of these problems, but is not yet in widespread use.
What do DNS resolvers do?
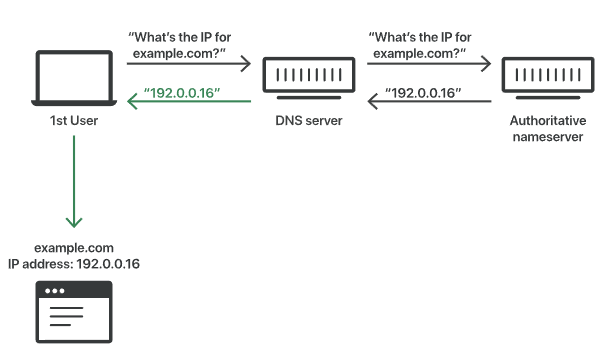
DNS resolvers provide clients with the IP address associated with a domain name . In other words, they take addresses from human-readable websites like “cloudflare.com” and translate them into machine-readable IP addresses. When a user tries to navigate to a website, their operating system sends a request to a DNS resolver. The DNS resolver responds with the IP address and the web browser takes the address and starts loading the website.
How does DNS caching work?
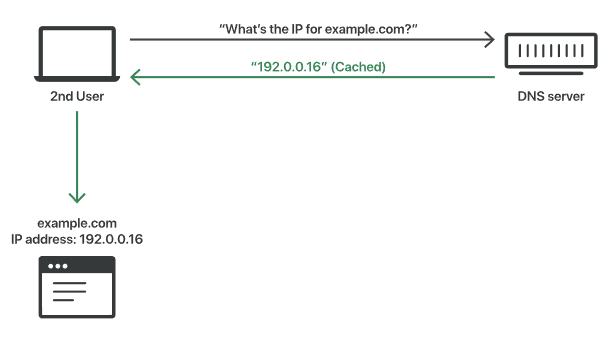
The DNS resolver will save responses to IP address queries for a set period of time. This allows the resolver to respond much faster to future queries, without having to communicate with the many servers involved in the typical DNS resolution process. DNS resolvers cache responses for as long as the time to live (TTL) associated with that IP address allows them to do so.
Uncached DNS response:
Cached DNS response:
How do attackers poison DNS caches?
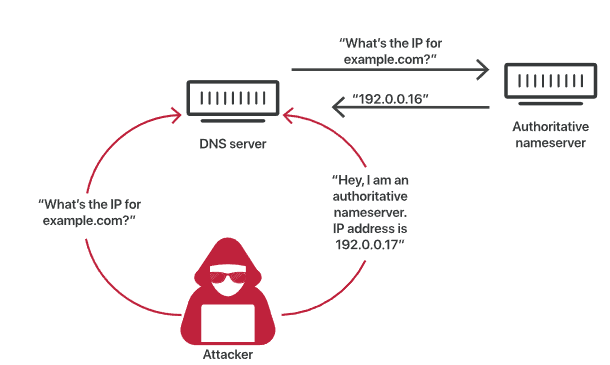
Attackers can poison DNS caches by impersonating DNS nameservers , making a request to a DNS resolver, and then spoofing the responses when the DNS resolver queries a nameserver. This is possible because DNS servers use UDP instead of TCP and because there is currently no verification of DNS information.
DNS cache poisoning process:
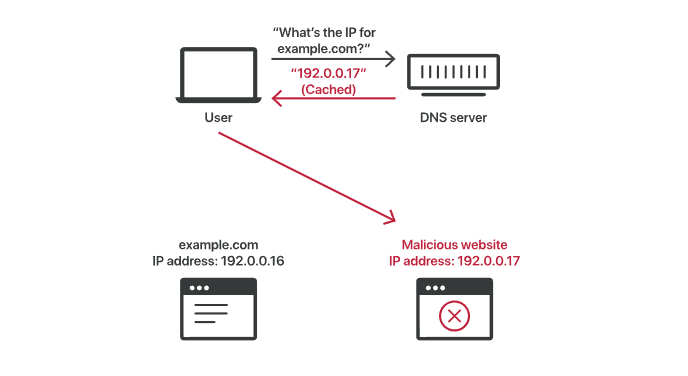
Poisoned DNS cache:
Instead of using TCP, which requires the two communicating parties to perform a ‘handshake’ to initiate communication and verify the identity of the devices, DNS requests and responses use UDP, or User Datagram Protocol. . With UDP there is no guarantee that a connection is open, that the recipient is ready to receive, or that the sender is who they say they are. For this reason, UDP is vulnerable to forgery; an attacker can send a message using UDP and pretend it is a response from a legitimate server by forging header data.
If a DNS resolver receives a spoofed response, it accepts and caches the data uncritically, since it is not possible to verify if the information is accurate and comes from a legitimate source. The DNS was created in the early days of the Internet, when only universities and research centers had access to it. There was no reason to expect someone trying to spread false DNS information.
Despite these serious points of vulnerability in the DNS caching process, DNS poisoning attacks are not easy. Because the DNS resolver actually queries the authoritative nameserver, attackers only have a few thousandths of a second to send the fake response, before the real response arrives from the authoritative nameserver.
Attackers also need to know or guess a number of factors in order to perform DNS spoofing attacks:
- Which DNS queries are not cached by the DNS resolver they want to attack, so that the resolver queries the authoritative nameservers
- Which port* is the DNS resolver using, they used to use the same port for every query, but now they use a different random port each time
- The request ID number
- Which authoritative nameservers the query will go to
Attackers could also gain access to the DNS resolver in another way. If a malicious third party operates, hacks, or physically accesses a DNS resolver, they can more easily tamper with cached data.
*In networks, a port is a virtual communication reception point. Computers have multiple ports, each with its own number, and in order for computers to communicate with each other, certain ports will need to be designated for certain types of communication. For example, HTTP communications always go to port 80, and HTTPS always uses port 443.
DNS spoofing and censorship
Several governments have intentionally poisoned DNS caches within their countries to deny access to certain websites or web resources.
I hope it will help you.





