In a world where cyber threats change and evolve at practically the same speed as technology itself, security solutions are needed that not only react to the threat, but are able to anticipate it. Within those proactive solutions we have the EDR system; In this article we explain what it is, how it works and how it can improve the cybersecurity of your company.
¿What is an EDR?
An EDR is a system for protecting and monitoring the company’s internal network and endpoint equipment ( those devices from which employees connect to the network in a way remote, ranging from computers to smartphones and tablets ).
The EDR mean precisely Endpoint Detection Response ( detection and endpoint response ) and is a security solution that combines different tools to monitor, analyze, anticipate and resolve threats that may put employees’ internal network and endpoint devices at risk.
A EDR software aims to reinforce the endpoint security of the company, as well as keep the internal network secure, configuring itself as a proactive solution, capable of detecting risks and threats that may exceed the first line of defense, which is usually the traditional antivirus and the firewall of the equipment that the employee uses to connect to the company network.
The EDR emerged as a response to more sophisticated threats, especially those that have emerged within the context of cyber warfare ( starring both companies and countries ), and the role that the user often plays as an entry point for different types of malware.
¿How does an EDR work?
An EDR system employs different types of tools, but with one common goal, to monitor the events of endpoint devices and the internal network to detect and report any type of threat. In addition, it creates a registry and a database that helps it detect, analyze, investigate, make reports and issue alerts.
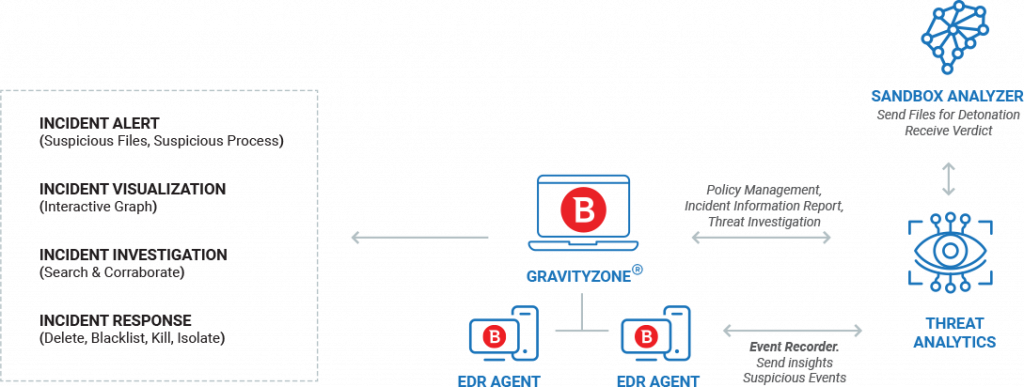
That is, an EDR system protects the network and equipment in real time, but also with subsequent analyzes of those suspicious events that it has blocked and isolated.
For example, when you detect suspicious behavior ( an email with an attachment ), it records it and takes you to an isolated environment to analyze its behavior, running it like a user would. If the attachment turns out to contain malware, it will block the mail that contains it on all systems and report the finding.
Thus, the EDR system is based on:
- Detecting a wide variety of threats, not just malware, such as phishing attempts, polymorphic viruses, or inclusion in a botnet.
- Containment of those threats that it detects in real time.
- Rapid investigation of security incidents, to solve them and minimize their impact. In addition, it conducts forensic analyzes that the IT team will use in its own investigation of a security incident.
- The elimination of threats on endpoint equipment and from the network itself.
Furthermore, thanks to the use of AI, machine learning and Big Data, the EDR system is able to learn automatically, so if the threat is repeated, You will know how to recognize it and respond to it appropriately.
¿What tools does an EDR security system use?
As we said, EDR security systems use various tools to be able to anticipate many of the existing threats beyond traditional malware, such as social engineering attacks, persistent advanced threats ( APT ), zero day vulnerabilities, user account commitment, the fileless malware or even threats not yet known or not based on signatures.
Thus, among the tools that we can find in an EDR we have:
- The aforementioned IA and machine learning.
- Sandbox environments for isolation and checking the detected threat ( not to be confused with the Privacy Sandbox from Google ).
- Create black and white lists for emails, IP addresses and web pages.
- Ability to integrate and operate alongside antivirus and other security tools.
- Tools to monitor systems and networks in real time, in addition to collecting information and then using it in future analyzes.
- Forensic analysis tools to investigate security incidents that have already occurred.
- Alert system, capable of filtering false positives and not overwhelming the IT team.
Advantages of an EDR system
Opting for an EDR system for our company can give us the following advantages:
- By automatically collecting and storing information from both endpoint devices and the network itself, you are able to create your own automated detection patterns, which helps in the threat detection process itself.
- Since it monitors the entire system in real time ( or practically in real time ), It can detect suspicious access attempts or data movements and thus stop the threat before they fully materialize.
- Collects all information regarding incidents or suspicious events or actions at a single point, allowing for a faster investigation.
- Its tools allow it to have a better capacity to anticipate threats and targeted attacks.
- Create a second line of defense to curb threats that manage to cross a first security solution, such as antivirus.
EDR use cases
The EDR is especially used to deal with those threats and cyberattacks than other tools more focused on reaction, that is, acting once they recognize the threat within the team, they cannot detect.
So the EDR is especially effective in detecting social engineering attacks, such as the aforementioned phishing or speaking phishing, to get user credentials with which to access the system and start moving through it or stay hidden and latent until the moment you decide to act.
It is also effective in detecting malicious or suspected attachments, such as Word or PDF documents with macros that include malicious code ready to run the moment the user opens it. As well as for the detection, as we already mentioned, of the fileless malware ( that runs from memory ) or of polymorphic viruses, that are changing shape to circumvent security measures.
EDR is also useful in the case of zero-day vulnerabilities and in the detection of exploits.
In short, the EDR system can complement and reinforce security systems based on more traditional solutions, on those remote-use equipment.
Relationship between EDR and Endpoints security
Obviously, the relationship between EDR and endpoint security is that it is a system created precisely to reinforce the security of remote connection devices.
With the increase in teleworking or remote work, it has been necessary to reinforce the security of the company’s internal network, but that is a measure that remains lame, if you are not also careful about the security of the devices that employees use to connect to said network and that are the entry point of many of the current threats.
Partly because many employees use personal equipment to work from home, and these generally do not have very powerful security solutions, beyond a possible antivirus and a possible firewall, not to mention the possible lack of software update.
Furthermore, cybersecurity is still a pending issue when it comes to training and awareness in many companies, with workers opening malicious emails and downloading and opening infected attachments, that can end up spreading throughout the internal network, with dire consequences.
Thanks to the EDR, those threats that manage to penetrate the antivirus and the firewall can be detected and contained or, at least, mitigated, avoiding waste of time, money and information for the company.
¿ERD or antivirus? Differences
Rather than talking about EDR or antivirus, we would have to talk about EDR and antivirus, since this second can be, as we have seen, one of the tools used by the EDR to detect known malware.
In any case, the main difference between an EDR and an antivirus is that the first is a security solution that covers all endpoint equipment and the company’s own internal network, and the second is an individual security solution, which is applied on a single computer.
Another difference is in what they can detect; We have already seen that EDR has the capacity, thanks to the use above all of machine learning, to detect a wide variety of threats, including those that are not based on signatures or are known. An antivirus only detects those threats that are known or based on signatures, although for this it must be updated to its latest version. While an EDR can detect an attempt to phishing what unfold a ransomware, an antivirus will only detect, if it does, when we have inadvertently installed it on the computer.
EDR vs. EPP
Before we see differences or which one is better, let’s see what a Endpoint Protection Platform ( EPP ) or endpoint protection platform. It is a system that groups several security tools, including antivirus, firewall, data encryption, detection of threats and prevention of unauthorized access at the endpoint or on the internal network.
Therefore, the EPP’s mission is perimeter protection, that first line of defense before EDR. So more than facing each other and choosing one of the two security solutions, the ideal would be to have both, since they complement each other where one of the systems does not arrive.
Thus, the EPP system will prevent the entry of known threats through the endpoints and the EDR will take care of all those threats that manage to penetrate that perimeter, such as the aforementioned social engineering attacks or APTs.
In fact, it is possible to find cybersecurity companies that offer tools that combine these two systems as a comprehensive security solution for endpoint devices and the company’s internal network.
Conclusions
Despite the EDR security o EDR security was born as a solution specially designed for large companies and organizations that had a dedicated SOC ( security operations center ), It has now become a security system in which any SME should consider investing, especially if it has many employees working remotely.
Even with an EPP system, we have already seen that the EDR would further strengthen the company’s cybersecurity, since it can detect those threats that the EPP overlooks or is not capable of recognizing, especially those that involve the human factor.
It is true that implementing an EDR system is a considerable investment, but in the long term it could avoid higher expenses associated with security incidents, such as ransomware, the leakage of data and information or the sanctions that the control authorities can impose in the face of certain security breaches, not to mention the consequences on the loss of reputation and trust of users or customers.
The increase in teleworking should not mean an increase in the risks to which the company is exposed, but for this it is necessary to apply security measures, like those offered by an EDR system.





