Systems and security engineer.
Gamer in my spare time.
I want to share everything about the world of technology in a way that is easier to understand and bring it closer and closer.
In this series, I’m going to write about some basics in Linux kernel exploitation that I’ve learned over the past few weeks: from basic environment configuration to some popular Linux kernel mitigations, and their corresponding exploitation techniques. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the only purpose of learning. We do…
Many people are asking me about Active Directory attack prevention methods and a good way for a critical vulnerability scan, which then leads me to get the domain administrator in fifteen minutes by simply exploiting misconfigurations in AD. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the only purpose of learning. We…
Nowadays we all know what an antivirus is, we know what we must have to stop a virus from entering our computer and making it unusable. The basic theory is fine, but to really know in depth what an antivirus does? I will explain in depth what it is and the reason for having it.…
Short for Server Message Block, SMB is an application layer protocol that enables file, printer and device sharing and inter-process communication (IPC) between applications on a network through a client-server architecture. In other words, computers (SMB clients) on a network can connect to SMB servers to access shared files and directories or perform tasks such…
Command injection is a cyberattack that involves the execution of arbitrary commands on a host operating system (OS). Typically, the threat actor injects the commands by exploiting an application vulnerability, such as insufficient input validation. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the only purpose of learning. We do not promote…
What is a CASB? According to Gartner, a cloud access security broker (CASB) is a security policy enforcement point, either on-premises or in the cloud, located between cloud service consumers and cloud service providers, whose purpose is to combine and enforce corporate security policies when accessing cloud resources. The CASB is like a policeman enforcing the laws…
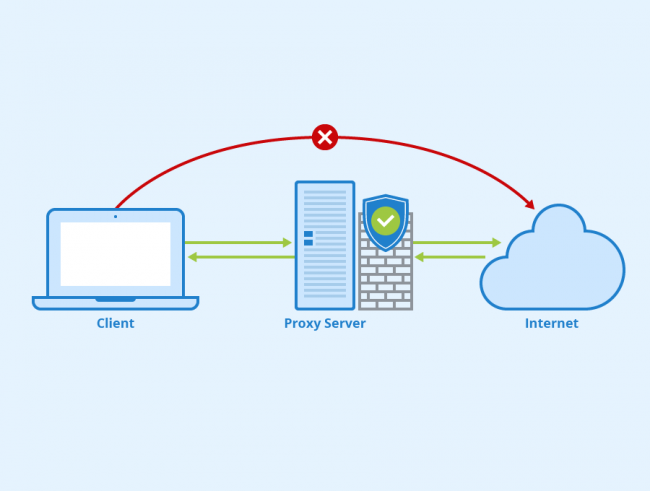
A proxy is a well-known technology in the market, although sometimes it is not well understood how it works. Therefore, in this opportunity we will explain what a proxy is and how it is useful. But before we start talking about the logical structure of proxy servers, I consider it important to clarify how it…
Code injection is the general term for attack types that consist of injecting code that is then interpreted/executed by the application. This type of attack takes advantage of mismanagement of untrusted data. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the only purpose of learning. We do not promote its use for…
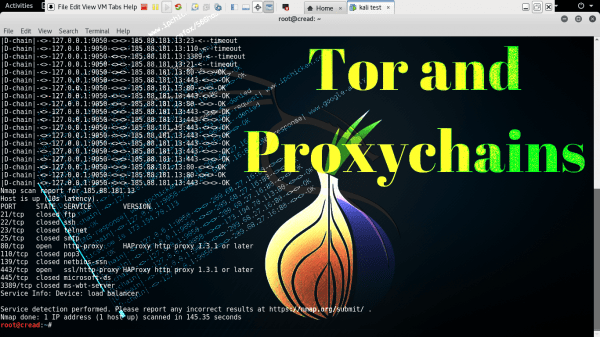
Proxychains is an open source software for Linux systems and comes pre-installed with Kali Linux, the tool redirects TCP connections through proxies such as TOR, SOCKS4, SOCKS5, and HTTP (S) and allows us to chain proxy servers. With proxychains, we can hide the IP address of the source traffic and evade IDS and firewalls. Requirements:…
Surely more than one has happened to you that you have forgotten the password of your windows or a Windows 10 that was in domain is not able to access the AD. In this tutorial I will show you how to enter the machine without knowing the password, either physical or virtual machine (in this…