SMB What is it and how does it work?
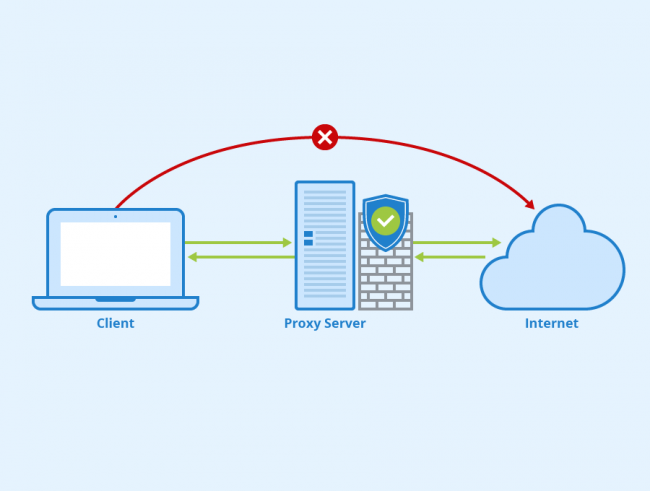
Short for Server Message Block, SMB is an application layer protocol that enables file, printer and device sharing and inter-process communication (IPC) between applications on a network through a client-server architecture. In other words, computers (SMB clients) on a network can connect to SMB servers to access shared files and directories or perform tasks such…