No matter how often you connect and how or why you mainly use the Internet, you have probably seen phishing attack attempts. They are now so common and problematic that cybersecurity professionals regularly provide information to help people detect and avoid phishing attacks.
Requirements:
- System – A system for testing
- Programming – High programming knowledge
Reposability:
In this tutorial we will use hacking techniques, for the sole purpose of learning. We do not promote its use for profit or incorrect purposes. We are not responsible for any damage or impairment that may be generated in the systems used. The responsibility is absolute of the user of this tutorial.
Knowledge:
- Linux – Low
- Programming – High
- Kali Linux – Low
- Windows – High
- Networks – Very high
General level of the Tutorial: High
Ideal for: Systems Engineers, Security Engineers, Pentesters
Phishing can be extremely harmful and have widespread consequences for victim organizations, including financial loss, data theft, and serious and lasting reputation damage. For this reason, many cybersecurity teams have internal training that tests how employees respond to phishing attacks. Cybersecurity teams use phishing training tools to send counterfeit emails, create fake login pages, and behave like genuine scammers would.
Kali Linux is a Debian-based open source Linux platform for digital forensic analysis and penetration testing. Using open source tools with it allows people to run phishing simulations. The results of those efforts can illuminate vulnerabilities and indicate what leaders must do to make phishing attacks less likely. This article will demonstrate how you can conduct your own email phishing training using open source tools at Kali Linux to improve your organization’s security posture and protect against cyber attacks and data violations.
¿What is email phishing?
Email phishing occurs when cybercriminals create fake emails for recipients to provide personal data and confidential information that malicious parties may exploit later. Phishing targets generally receive messages with at least one urgent element. They can warn people to give the requested details to avoid a lost package delivery, late payment, or unfulfilled order. Some phishing attacks take a positive approach, urging people to provide information in exchange for alleged awards or funds.
If the victim falls in love with her, she usually clicks on a link that redirects them to a page to provide details. Some phishing attacks ask people to download seemingly harmless files containing malware. Then associated viruses can infect entire networks. Evidence also suggests that it pays cybercriminals to focus on phishing attacks. Because phishing attacks are very successful in tricking victims into sharing sensitive credentials with attackers or downloading harmful malware 90% of modern cyber attacks start with a phishing email.
Best email security practices to protect against phishing attacks
Whether you are an individual user or involved with organizational cybersecurity, it is vital to participate in best email security practices that will keep you safe while setting a good example. Here are some to strongly consider:
- Avoid immediately relying on any email, even if it seems legitimate.
- Learn the revealing features of phishing emails.
- Never click on suspicious links or attachments.
- Use electronic signatures for documents sent by email when appropriate.
- Schedule regular employee training sessions and phishing simulations.
- Apply a spam filter to email system to filter malicious content.
- Stay on top of all known and emerging phishing threats.
- See phishing prevention as everyone’s responsibility.
- Implement a Adaptive Cloud Based Comprehensive Email Security Solution.
Following fundamental steps does not stop all attacks, but makes them significantly less likely to happen. Also, when people know that an organization takes phishing prevention seriously, they will see its role in recognizing and stopping such attacks.
¿Why is safety awareness training essential?
Security Awareness Training ( SAT ) is an organization-wide effort that helps people identify and protect themselves against cyber threats at work and when using Internet at home. It is an integral part of cybersecurity defenses ’ organizations.
Consider a 2022 study that exposed participants to five categories of emails. The results found people generally had trouble recognizing modern phishing attacks. Although 50% identified the red spelling and grammar flags of phishing email, people’s responses were more varied when phishing signs were less obvious or more ambiguous.
Organizations must implement SAT because human error is an element in most cyber attacks. People who organize phishing attacks know how to take advantage of what people want and what they are most likely to believe. In addition, many people work in high pressure environments with numerous expectations placed on them. Those realities may mean that they don’t take enough time to study emails to determine validity. However, if people receive continuing education about what constitutes a phishing attack, They will be more alert to suspicious features and know that they should not interact with emails that have them.
It is also essential that any SAT effort focus on online threats. Some people spend dozens of hours online weekly, so it is highly likely that they will eventually encounter dangers on the Internet. Security awareness training will well train each employee to detect and avoid threats. As a result, organizations have better protection against cyber attacks that could stop operations, cause them to lose money and customers, or means that the company must recover from reputation damage.
How to do your own email phishing training
Internal testing and training will help people become more aware and avoid common phishing email strategies. Fortunately, Kali Linux offers you great options for open source tools that make phishing training easier. We will cover many of them below.
Phishing training in your business allows you to create authentic examples of phishing attacks and see how employees respond to them. Then you can find gaps in worker awareness ’ and focus on the next training sessions.
Kali Linux Email phishing training tools
Kali Linux is an open source distribution aimed at people who must perform penetration tests and perform security audits. Comes with more than 600 penetration test tools. Kali Linux is also completely free and customizable to meet the needs of ’ users. Now, let’s look at various phishing tools for Kali Linux.
PhishMailer
PhishMailer allows you to create email templates that seem to come over 20 well-known companies. This tool requires Python 3 and its developers tested it on Kail Linux. It has an easy to use interface, but a potential disadvantage is that there have been no updates for a couple of years.
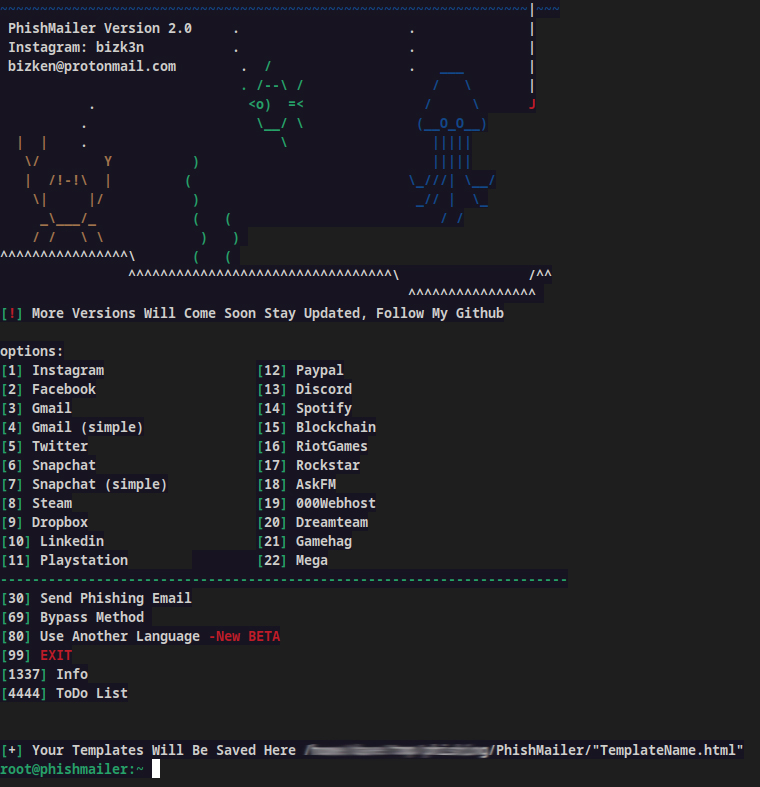
Install it by cloning the repository with the git clone command:
git clone https://www.github.com/BiZken/PhishMailer.git
The following command will install it and allow you to access the tool directory.
cd Desktop
git clone https://www.github.com/BiZken/PhishMailer.git
cd PhishMailer/
Now that you have downloaded the tool, run it with the following command:
python3 PhishMailer.py
Then you will have the opportunity to enter several pieces of information about your phishing goal.
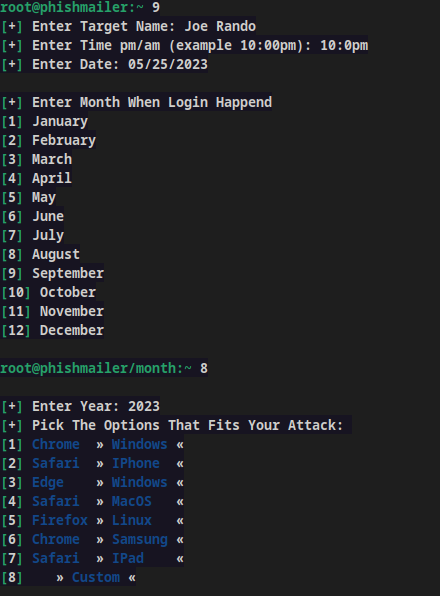
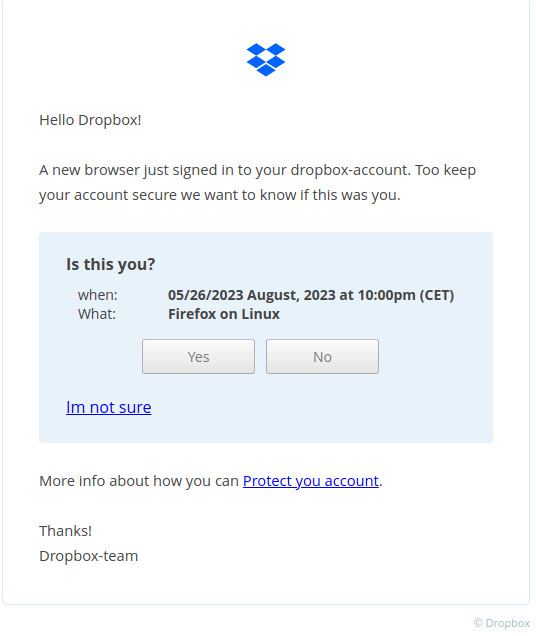
The tool will then generate a link that you can open in a browser. Once a phishing destination enters your email and password on the fake page, you will get relevant details, as seen below.
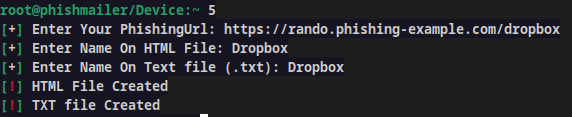
Within two minutes of installation, I was able to create this Dropbox sample phishing message. Each of the links in this screenshot ( including the link “ I’m not sure ” ) direct to my sample phishing site.
BlackPhish
BlackPhish es una herramienta de simulador de correo electrónico de phishing robusta pero ligera. Sin embargo, un inconveniente es que todavía está en beta, por lo que pueden surgir numerosos problemas durante el uso. Los desarrolladores lo probaron en Kali Linux 2019.4, pero las comprobaciones de compatibilidad en otras plataformas están en curso. BlackPhish tiene seis plantillas de correo electrónico, junto con una interfaz fácil de usar.
Instale BlackPhish moviéndose al escritorio y usando el siguiente comando:
cd Desktop
git clone https://github.com/iinc0gnit0/BlackPhish
Mientras esté dentro del directorio de la herramienta, continúe la instalación con el siguiente comando:
cd Blackphish
sudo bash install.sh
Finalmente, ejecute BlackPhish con el comando:
sudo python3 blackphish.py
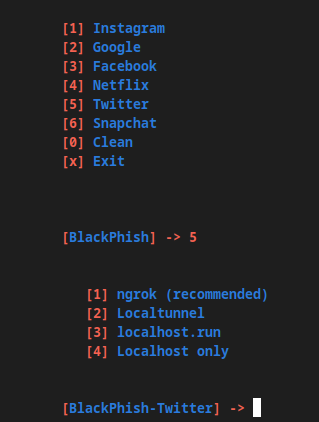
After doing that, you will reach the main screen. Choose the type of phishing simulation you want to perform by pressing its corresponding number and the Enter key.
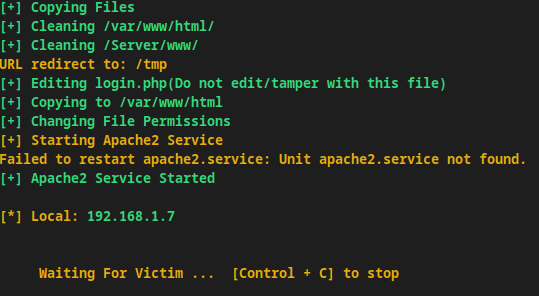
Progressing through the steps will give you more options to customize the content and you will preview what the simulated message will look like for users. Eventually, you will receive relevant information if someone falls in love with the phishing trick.
Final thoughts on Kali Linux Open source phishing training tools
Whether your organization has five or 500 team members, phishing testing and training are essential to minimize cyber risk. Even if most employees know many of the characteristic signs of phishing attempts, cybercriminals frequently update their methods, which can mislead many victims.
As you evaluate phishing training tools, prioritize those that allow you to make messages apparently from various popular platforms. Then, when considering how to make content as realistic as possible, modify the messages to determine which phrases are most credible to the target audience. Also realize that people of certain ages and backgrounds may be more or less likely to fall for phishing attempts than others.
Before considering whether to use a tool, spend time using and getting familiar with it. Then you will know better if you will meet your goals and expectations. Finally, remember that phishing training is not a unique exercise. Making it a regular part of cybersecurity enhancement and readiness will help you assess how people’s understanding of phishing evolves.