Short for Server Message Block, SMB is an application layer protocol that enables file, printer and device sharing and inter-process communication (IPC) between applications on a network through a client-server architecture. In other words, computers (SMB clients) on a network can connect to SMB servers to access shared files and directories or perform tasks such as printing over the network.
Background
SMB was created by IBM in 1984 for local file sharing. Over time, multiple variations of the SMB protocol were developed to enhance its features and meet evolving network and security requirements. In general, SMBv2 reduced the chatty nature of the protocol and SMBv3 provided further performance improvements and strong end-to-end encryption. The following is a brief summary of the SMB versions:
- SMBv1: The first version of SMB was released in 1984 by IBM for DOS file sharing.
- CIFS: With Windows 95, Microsoft released an updated version of SMBv1 and renamed it CIFS, short for Common Internet File System.
- SMBv2: With Windows Vista, Microsoft released SMBv2, which came with notable performance improvements and increased efficiency.
- SMBv2.1: With Windows 7, SMBv2.1 was released with further performance improvements.
- SMBv3: With Windows 8, SMBv3 was released with significant security updates, including end-to-end encryption.
- SMBv3.02: With Windows 8.1, SMBv3.02 provided further security improvements, especially the ability to disable the insecure SMBv1.
- SMBv3.1.1: In 2015, with Windows 10 and Windows Server 2016, the latest version of SMB was released, SMBv3.1.1. This version provides protection against man-in-the-middle attacks and supports AES-128-GCM (Advanced Encryption Standard-128-bit) encryption and implements preauthentication integrity checks using SHA-512 (Secure Hashing Algorithm).
How does the SMB protocol work?
To begin with the communication model, SMB operates on a client-server architecture. In this model, SMB servers provide network resources, such as files or printers, to other computers, known as clients. Thanks to this feature, users from different remote devices can collaborate on shared files and print their documents on shared printers across a network.
In addition to this core functionality of shared files and printers in the services, SMB also provides authenticated interprocess communication (IPC) between processes running on remote computers. For this purpose, a network share, known as an IPC share (ipc$), is used on Windows computers to facilitate communication between processes and remote computers.
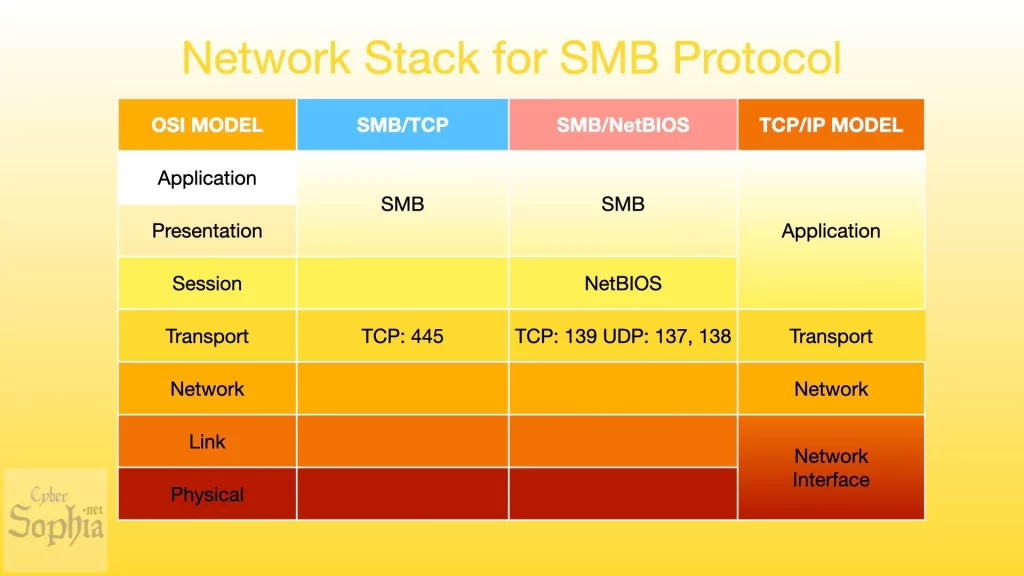
With respect to the OSI model, SMB operates at layer 7 as an application layer protocol and relies on lower level protocols for transport. In early versions of Windows, SMB ran on top of the NetBIOS protocol and used ports 137, 138 and 139 (UDP ports 137, 138 and TCP ports 137, 139). As a session layer protocol, NetBIOS (layer 5 in the OSI model) allows applications to communicate over a local area network (LAN) with device-specific NetBIOS names in addition to IP addresses. However, since Windows 2000, the SMB protocol runs directly on TCP/IP and uses port 445.
What is Samba?
SMB is a Windows-specific protocol and non-Windows computers or servers on a network cannot interact with Windows computers via SMB.
For this reason, an open source implementation of the SMB protocol, known as Samba, was released in 1992 for Unix and Linux devices. It supports similar features to SMB, but can communicate not only between Unix/Linux devices and servers, but also with Windows clients.
What types of services does the SMB protocol represent
The SMB protocol, which corresponds to the appropriate and representative levels of the OSI model, regulates the interaction of the workstation with the server. The SMB function includes the following operations:
- Session management. Creating and breaking a logical channel between a workstation and the network resources of a file server.
- File access: The workstation can access the file server with requests to create and delete directories, create, open and close files, rename and delete files, search for files, retrieve files and install files.
- Print service. The workstation can queue files on the server and get print queue information.
- Messaging service. SMB supports simple messaging with the following functions: send a simple message, send a broadcast message, send the beginning of the message block, send the text of the message block, send the end of the message block, send the user name, cancel sending, get the host name.
- At a high level, the representation of the SMB protocol is quite simple. It includes all possible operations for working with files and printers that are used on a normal computer.
Safety issues and concerns
Especially due to its wide range of features and its complex implementation (which is contrary to the principle of “Economy of Mechanisms”), quite a few SMB-related vulnerabilities were discovered over the years and some of them caused serious security problems worldwide.
The most infamous of these vulnerabilities were 5 Remote Code Execution (RCE) vulnerabilities (CVE-2017-0143, CVE-2017-0144, CVE-2017-0145, CVE-2017-0146, CVE-2017-0148) that affected Windows computers running SMBv1. Microsoft subsequently released a patch MS17-010) on March 14, 2017, however, experts advised users and administrators to take the additional step of disabling SMBv1 on all systems.
Just one month after patching the MS17-010 vulnerabilities, a hacker group called Shadow Brokers leaked (on April 14, 2017) the Eternal Blue exploit that was allegedly developed by the U.S. National Security Agency (NSA). Following this revelation, two infamous malware programs were detected to be spread via the Eternal Blue exploit. First, the global WannaCry ransomware attack took place in May 2017, affecting more than 200 000 unpatched computers. Then, a more devastating ransomware with the name NotPetya affected even fully patched computers in June 2017 with the EternalRomance and EternalBlue exploits. NotPetya caused more than $10 billion in damage according to a White House report.
To give recent examples, the following 2 notable SMB vulnerabilities affecting SMBv3.1.1 were discovered in 2020.
Safety measures
Given the WannaCry and NotPetya malware and several other vulnerabilities, including SMBGhost and SMBleed that were discovered in the most recent version of SMB (v3.1.1), many network administrators and security professionals are questioning whether or not it should be deployed on networks. In general, the latest, patched version of SMB is considered a secure protocol. However, to reduce any security risks due to SMB, the following measures should be taken:
- Do not use SMBv1 as it lacks encryption, is inefficient and due to its complex implementation other critical flaws similar to the MS17-010 vulnerabilities could appear in the future.
- Prefer the latest version of SMB (SMBv3.1.1 as of the date of this post) whenever possible. SMBv3.1.1 is more efficient compared to previous versions of SMB and provides state-of-the-art security features.
- As a security best practice (least privilege), access to SMB should be restricted to trusted networks and clients only.
- Last but not least, if SMB functionality is not required, SMB should be disabled on Windows platforms to reduce the overall attack surface and leak as little fingerprint information as possible to attackers.
I hope you liked the post and I hope it helps you.