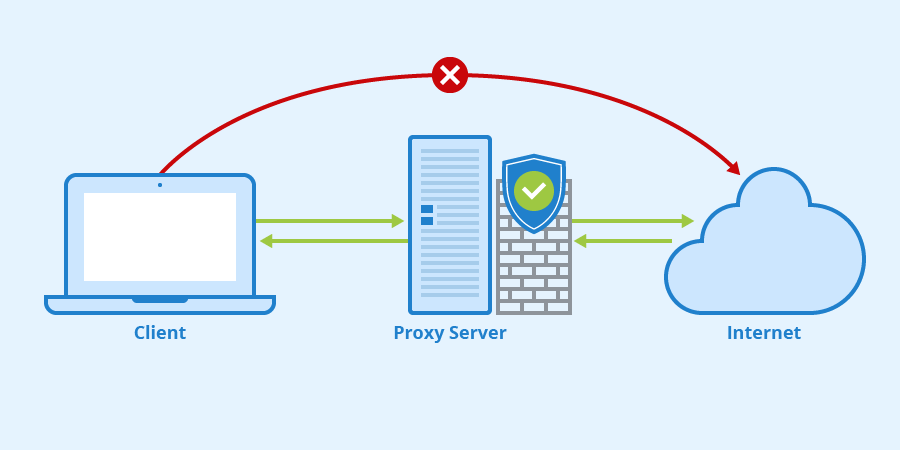
A proxy is a well-known technology in the market, although sometimes it is not well understood how it works. Therefore, in this opportunity we will explain what a proxy is and how it is useful. But before we start talking about the logical structure of proxy servers, I consider it important to clarify how it is physically implemented in a network environment, therefore, for this part of the explanation, take into account the following topology:
What is a Proxy?
Proxy servers are generally used as a bridge between the source and destination of a request. In our image, you can see that the computer needs to go through the proxy server to access the Internet, and this is one of the common uses of proxy servers.
For this article, let’s take the example of a fictitious company called ACME S.A . At ACME there is a server that allows Internet browsing, a proxy server, and without it it is not possible to browse the Internet at all. Therefore, all computers on the network must have the proxy address and their browser port configured for Internet access to take place.
What is a proxy server for?
In this case, the proxy can fulfill some of the following functions:
- Access control: Proxy server administrators may or may not allow certain users to access the Internet through restrictions on their own login or IP addresses, providing the environment with an additional layer of protection.
- Content filtering: being in the middle of the road, the server also allows, or does not allow, access to certain sites. Among the rules that can be applied are those for blocking specific websites, or even entire categories.
Example: the user Despreocupado da Silva is an employee of the company ACME, who can usually surf the Internet through the proxy, since his user has permission to do so. At a certain time of the day, Mr. Despreocupado tries to access the Facebook site and receives a blocking message indicating that access to the social network is blocked. After a few hours of the day, Despreocupado tries to access a few more sites, including some investment-related sites, but they are all blocked and display the message that the Investment/Finance category is not allowed.
In the case of Facebook, only one site was blocked, while, in the case of sites targeting the financial market, all are blocked considering that the entire category is part of the blocking rule.
- Caching: Another common use for Web Proxies is to have them perform a caching function. This causes the proxy, after accessing a page, to store the content of the page in its system. After that, other requests to this same page will not have to go to the Internet, because the content is already stored in the proxy’s memory.
To illustrate, Mr. Carefree accesses a website called www.123.com. Since the server was configured to cache, it stores all the content that Mr. Carefree accessed. After a few minutes, another user, Mr. Calm, also wants to access the same site (www.123.com). When he tries to access, the proxy does not even search the Internet to respond to the page request, as it has everything in memory and displays the cached site for Mr. Calm, thus saving ACME’s Internet usage.
These are widely used functions of a web proxy server and illustrate a commonly used scenario for most businesses.
Reverse proxy
Another very common use is reverse proxy servers. In the previous examples, the origin of the connection was always inside the network, passing through the proxy to the Internet. In the case of the reverse proxy, the origin of the requests is on the Internet and seeks access to a server within the environment, as shown below:

Reverse proxies are commonly used to handle requests to servers hosting web pages. Some of the benefits of using them in this way are:
- Load balancing: Because the structure of the reverse proxy server allows you to connect to multiple destination servers, you can direct requests to each of them without overloading any of them. As another security feature, requests from the Internet will know only the IP address of the proxy and not all the servers and pages that the company has.
- Caching: As in the web caching example, proxy servers are also used to optimize requests between source and destination. The reverse proxy server stores page elements stored on internal servers, checking for content updates from time to time, so that the page servers receive even fewer network requests, allowing them to perform even better.
Proxy for all
We cannot talk about proxy without talking about free proxies. These are websites, such as https://free-proxy-list.net/, that provide addresses of proxy servers all over the world “absolutely free of charge”. Anyone on the Internet can make the appropriate settings in their browser and use the offered server to surf the web.
If the question is what someone might want this for, the answers are varied. Using a proxy means that all requests are made through the proxy server, not your Internet link, so your Internet Service Provider (ISP) does not know what Internet destinations you are going to.
Warning: the phrase “completely free” is in quotation marks because, in general, companies and individuals who offer completely open proxy servers on the Internet are making some kind of profit. It is important to remember that, although the ISP does not have access to the addresses you access, the proxy server knows everything that users do and can use this information for a variety of purposes, such as distributing advertising, intercepting content for behavioral analysis, gathering information and other purposes, malicious or otherwise.
TOR
Tor (The Onion Router) is a tool that allows chained connection to multiple proxy servers, making it even more difficult to track the source of origin. It was designed to ensure access to information even for people in countries with severe government restrictions on access to content on the Internet and works similarly to proxy servers.
The other side of the coin
A Proxy is a tool and, like all tools, it can be used for both good and evil.
Cybercriminals often use proxy servers to commit crimes, as they connect the machines that will attack people with proxy services found on the Internet, such as free proxies or even the Tor network, and carry out their attacks. This makes it so that the victims they are attacking cannot identify the true origin of the attack, making it so that blocking rules cannot be properly created to prevent the attack from continuing.
Properly and consciously using the tools and resources offered to us gives us the possibility to build our security arsenal, but it is also important to remember that most tools can be used for a variety of purposes, so knowing what their downsides are can help us to configure and use them in a well-structured way.
I hope you like it and that it helps you.