Proxychains is an open source software for Linux systems and comes pre-installed with Kali Linux, the tool redirects TCP connections through proxies such as TOR, SOCKS4, SOCKS5, and HTTP (S) and allows us to chain proxy servers.
With proxychains, we can hide the IP address of the source traffic and evade IDS and firewalls.
Requirements:
- Kali Linux – Attacker
Responsibility:
In this tutorial we will use hacking techniques, with the only purpose of learning. We do not promote its use for profitable or improper purposes. We are not responsible for any damage or impairment that may be generated in the systems used. The responsibility lies entirely with the user of this tutorial.
Knowledge:
- Linux – Medium
- Programming – Not applicable
- Kali Linux – Medium
- Networks – Bass
Let’s get started:
To set up proxychains you will first need the tor service, most of the time the service is preinstalled. To check if the tor service is available or not, just use this command.
First change to ROOT user
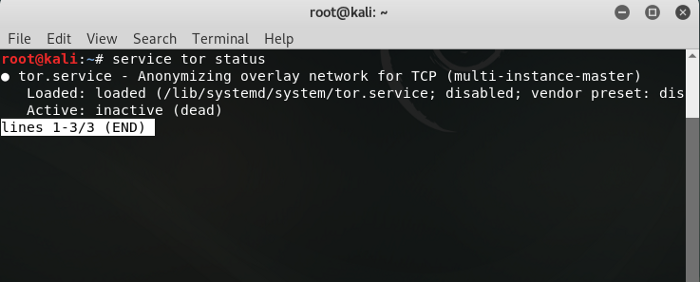
sudo -i root@kali:~# service tor satus
If you get this output it means that TOR is not installed on your system and is not running.
To install TOR
root@kali:~# apt-get install tor
We had already installed the tor service before, so there will be a difference in execution. If you get any errors doing this, then do update && upgrade and reboot, and do it again.
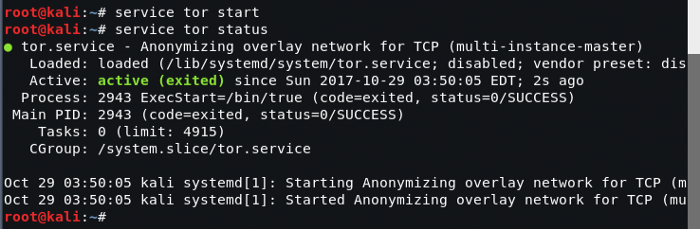
If TOR installs successfully, start the TOR service.
root@kali:~# service tor start
Now to check the status of the TOR service.
root@kali:~# service tor status
Configure proxychains
After installing the tor service we now need to configure proxychains. To do this use the following command.
Note: you must be in the ROOT user. if you are not then switch to Root.
root@kali:~# nano /etc/proxychains.conf
If you see this type of file in the terminal, you will see “#” which means comments in bash language. if there is no hash “#” means it is executed by default. or if we remove the hash “#” means we want to execute this. You can use the arrow keys to scroll down and up to read the contents of the file and make the following changes you need.
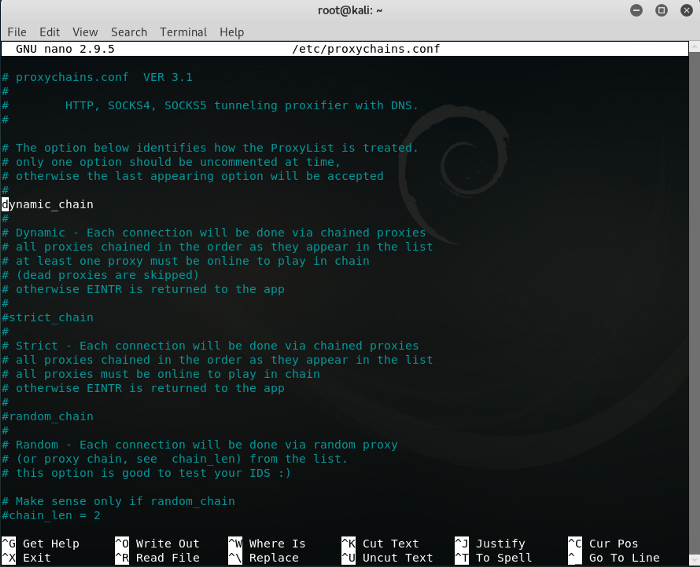
As you can see there are three types of proxychains: 1)dynamic 2)strict 3)random
we are going to use the dynamic string,
1 – remove the dynamic string from the comment
2 – comment out the strict string and the random string
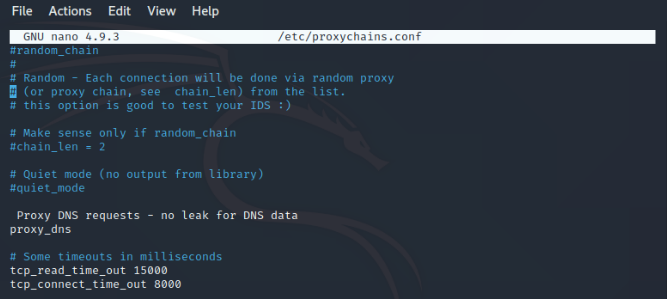
1 – Remove the DNS proxy from the comments
2 – In addition, remove the proxy DNS requests – no DNS comment data leakage
Tips: here the elimination of DNS proxy and no DNS data leakage, helps you to full anonymity.
3 – Now, type socks5 127.0.0.1 9050 in the last line of the proxy list.

Now just type save with ctrl+o and enter and to exit the file ctrl+X, now exit the terminal, the proxychains configuration is complete.
Tips: Here, SOCKS is an internet protocol that routes packets between a server and a client using a proxy server. and socks4 and socks5 is the type of socks.
127.0. 0.1 is the Internet Protocol (IP) loopback address, also known as localhost.
9050 is the port number and by default, Tor listens on this port for the socks proxy.
Now reboot your machine,
To start proxychains first restart the Tor service and then start proxychains in firefox with a link for a particular search engine like bing, duckduckgo. Use the following commands:
root@kali:~# service tor restart
To check that it works properly, open a console and enter:
proxychains firefox https://whatismyipaddress.com/
The console will be executed from behind like this:
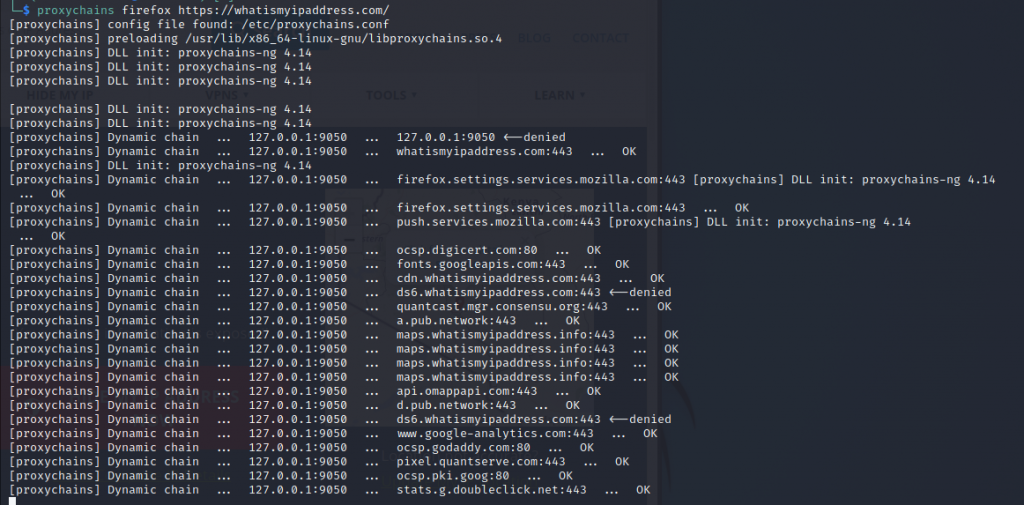
And when we open the browser, we can see where I am connecting:
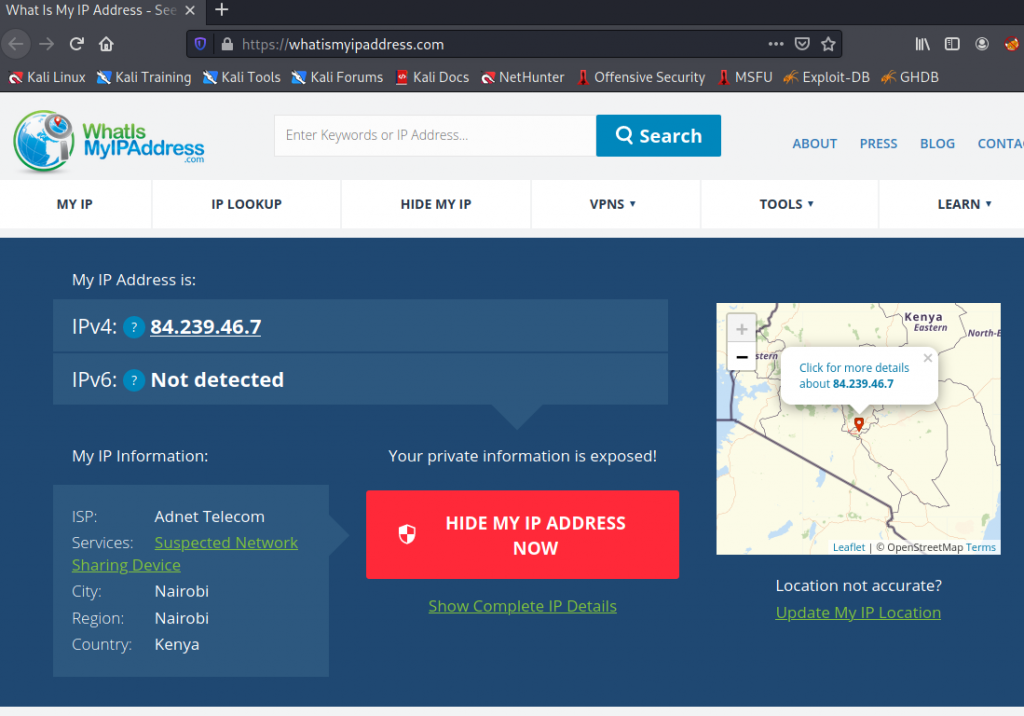
If we run the command again you can see that I come out of another location:
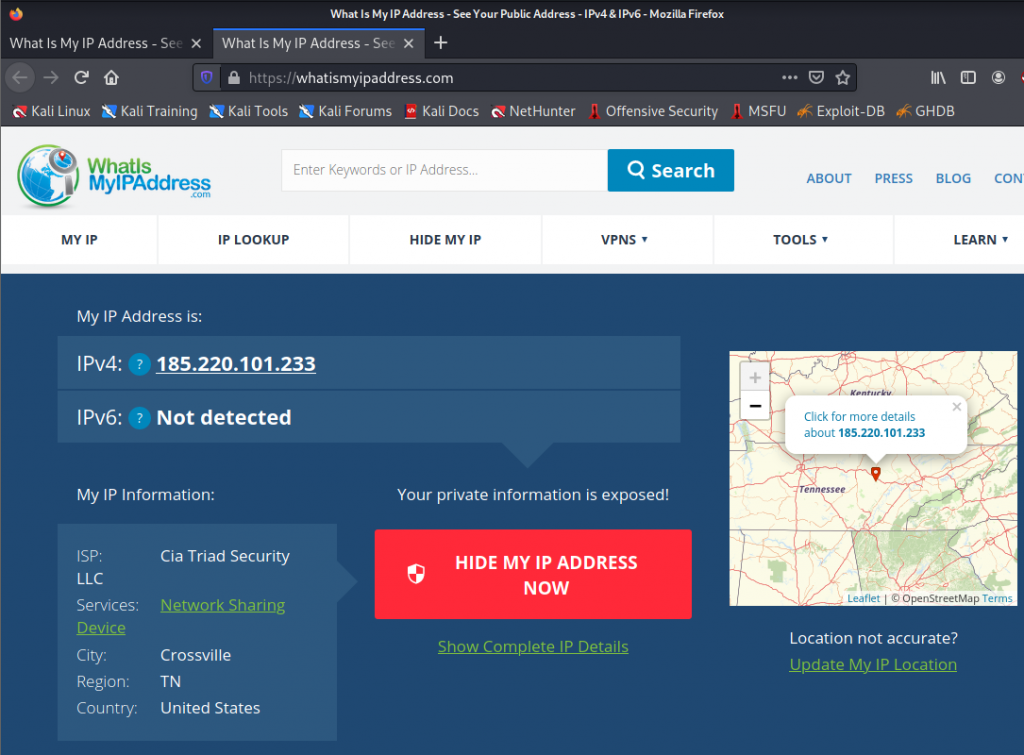
Many now wonder, is it just to hide my browser?
The answer is: NO
The TOR Proxychains application allows us to run any type of application that we have in Kali and thus the attacks to be totally anonymous.
For example:
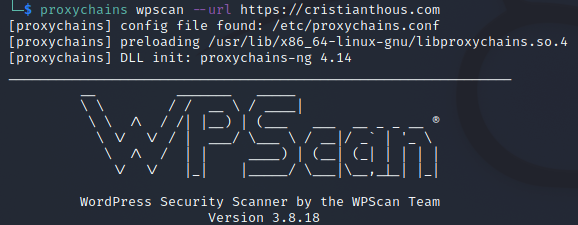
I can use applications such as: WPSCAN
proxychains wpscan https://cristianthous.com/
I hope you like this tutorial and find it helpful.







