Ingeniero de sistemas y seguridad.Gamer en los ratos libres.Quiero compartir con todo sobre el mundo de la tecnología de manera mas fácil de entender y acercarla cada vez mas.
Let’s face it: we all use email, and we all use passwords. Passwords create an inherent vulnerability in the system. The success rate of phishing attacks is skyrocketing, and opportunities for attack have multiplied enormously as life has moved online. All it takes is one compromised password for all other users to fall victim to…
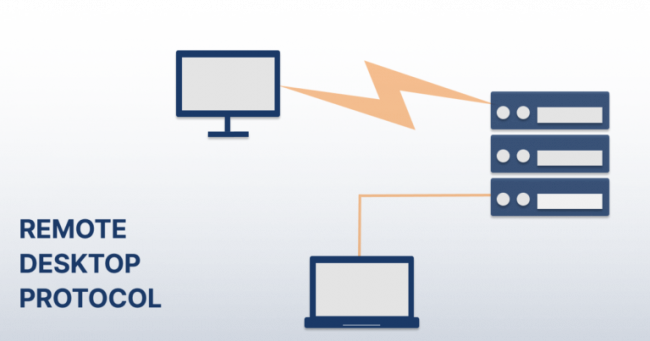
Remote Desktop Protocol (RDP) is a protocol, or technical standard, for using a desktop computer remotely. Remote desktop software can use several different protocols, including RDP, Independent Computing Architecture (ICA), and Virtual Network Computing (VNC), but RDP is the most widely used protocol. RDP was initially released by Microsoft and is available for most Windows…
With the support of the open-source community and a strict privilege system built into its architecture, Linux has security built into its design. That said, gone are the days when Linux system administrators could get away with poor security practices. Cybercriminals have come to view Linux as a viable attack target due to its growing…
Content spoofing (also known as content injection) is one of the most common web security vulnerabilities. It allows the end user of the vulnerable web application to falsify or modify the actual content of the web page. Requirements: Responsibility: In this tutorial, we will use hacking techniques for educational purposes only. We do not promote…
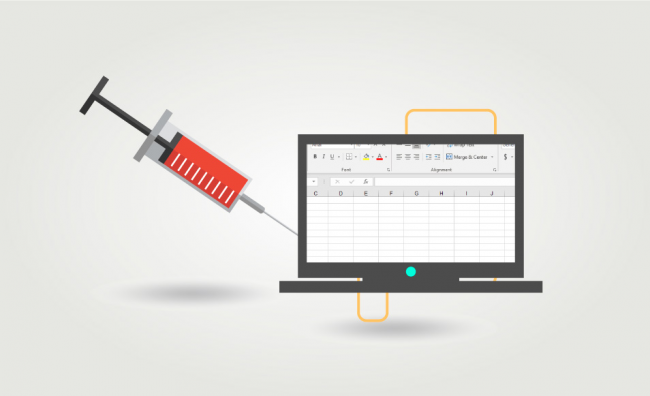
Online attacks are more frequent than ever, and this trend is likely to continue growing. In this article, we analyze CSV injection attacks and how to defend against them. Requirements: Responsibility: In this tutorial, we will use hacking techniques for educational purposes only. We do not promote their use for profit or improper purposes. We…
A script to remotely dump files and folders from a Windows SMB share Requirements: Responsibility: In this tutorial, we will use hacking techniques for educational purposes only. We do not promote their use for profit or improper purposes. We are not responsible for any damage or impairment that may be caused to the systems used.…
Today I bring you a very simple tutorial that many people have been asking me for. It’s about attacking Kerberos tickets, both golden and silver. First, to understand what Kerberos is, visit my post that talks about Kerberos Requirements: Responsibility: In this tutorial, we will use hacking techniques for educational purposes only. We do not…
Data exfiltration—also known as Data Exfiltration—refers to the unauthorized transfer of sensitive information outside a secure corporate environment. This risk has become one of the top security concerns, as it can lead to theft of confidential information, reputational damage, and significant financial losses. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the…
This tutorial provides an in-depth exploration of the LockBit ransomware, one of the most sophisticated and dangerous ransomware strains in 2024. This blog is designed for cybersecurity professionals, IT administrators, and businesses aiming to understand the mechanics of ransomware attacks and how to defend against them. It combines technical insights, practical attack simulations, and mitigation…
Cybersecurity is a top priority in the digital age, where cyber threats to systems and networks are increasing every day. One of the key tools for protecting computer systems is the Host Intrusion Detection System (HIDS). This article details how HIDS works, its benefits and provides practical examples for a better understanding. What is a…