Why Zero Trust Network Access (ZTNA) Replaces VPNs: Architecture, Security, and Operational Gains
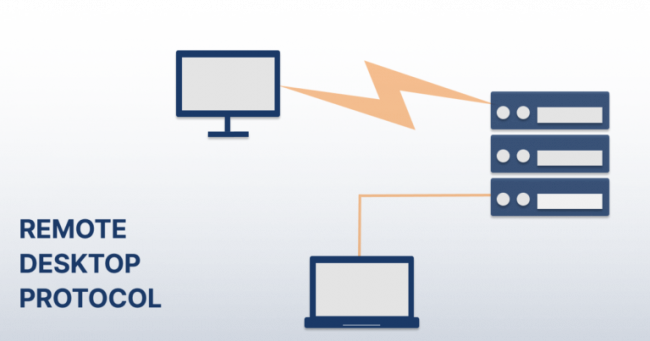
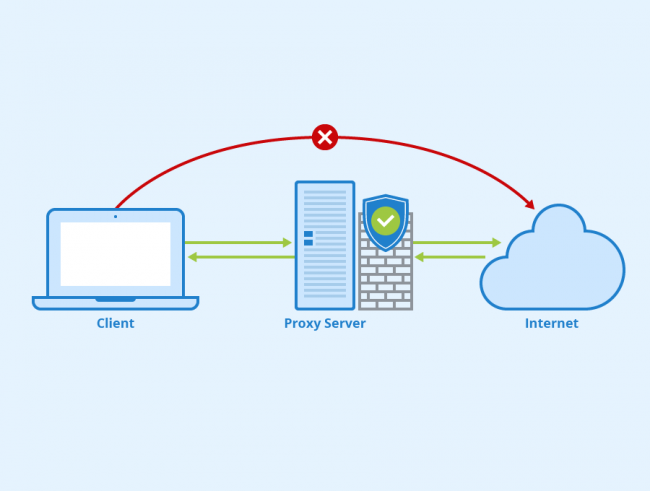
This technical playbook explains why Zero Trust Network Access (ZTNA) is the practical successor to legacy VPNs. Learn the architecture, core controls, SASE integration, and a phased migration plan to reduce attack surface, simplify operations, and improve security posture. Read on for actionable guidance to plan a safe, measurable ZTNA transition.