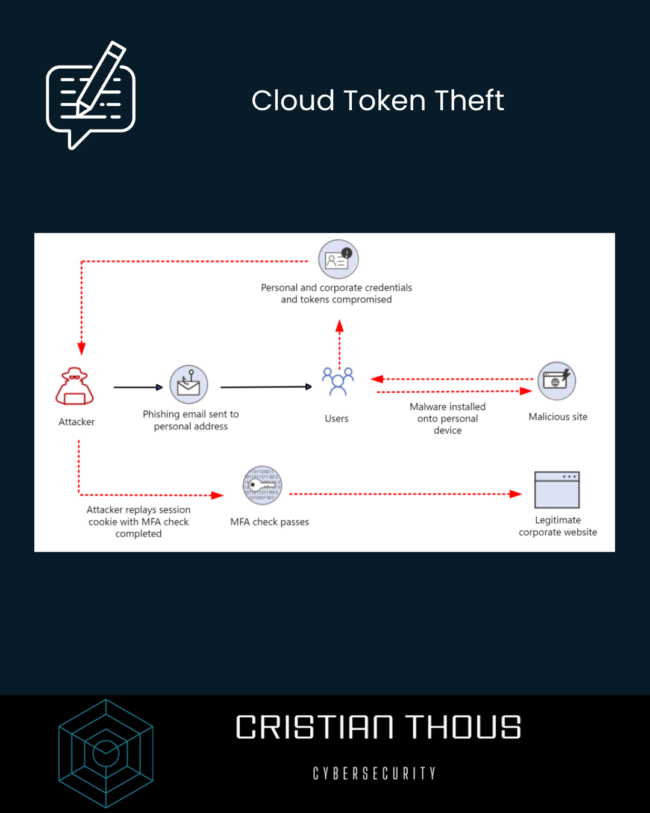
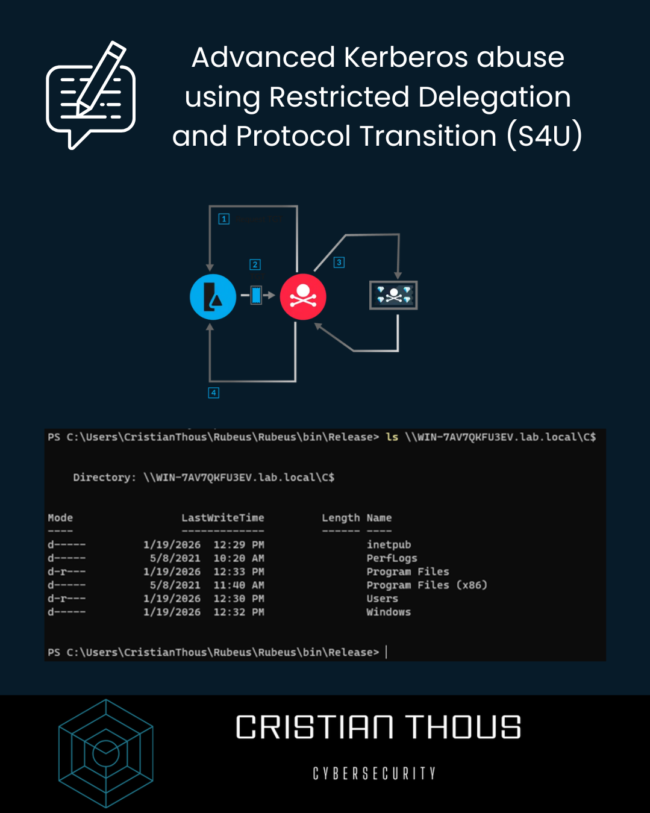
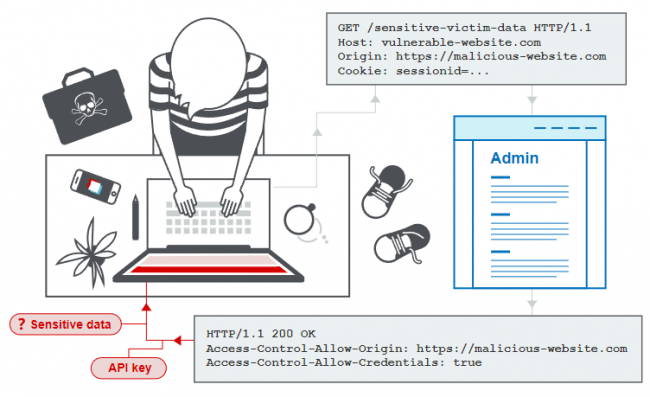
Cloud Token Theft
Introduction As organizations accelerate their migration to the cloud, identity has become the cornerstone of modern security architectures. Traditional network perimeters have dissolved, replaced by authentication and authorization mechanisms that rely heavily on tokens, sessions, and contextual trust. This evolution has significantly improved usability and scalability—but it has also introduced a new class of threats.…