Introduction
As organizations accelerate their migration to the cloud, identity has become the cornerstone of modern security architectures. Traditional network perimeters have dissolved, replaced by authentication and authorization mechanisms that rely heavily on tokens, sessions, and contextual trust.
This evolution has significantly improved usability and scalability—but it has also introduced a new class of threats. Among them, Cloud Token Theft stands out as one of the most dangerous and least understood attack techniques affecting modern cloud environments.
Unlike traditional credential-based attacks, Cloud Token Theft does not rely on stealing usernames or passwords, nor does it aim to directly bypass Multi-Factor Authentication (MFA). Instead, it exploits a fundamental assumption of cloud identity systems: that a valid token represents a trusted, authenticated user.
This article provides an in-depth, theoretical analysis of Cloud Token Theft—what it is, why it works, why it is so difficult to detect, and what it reveals about the limitations of current identity security models.
What Is Cloud Token Theft?
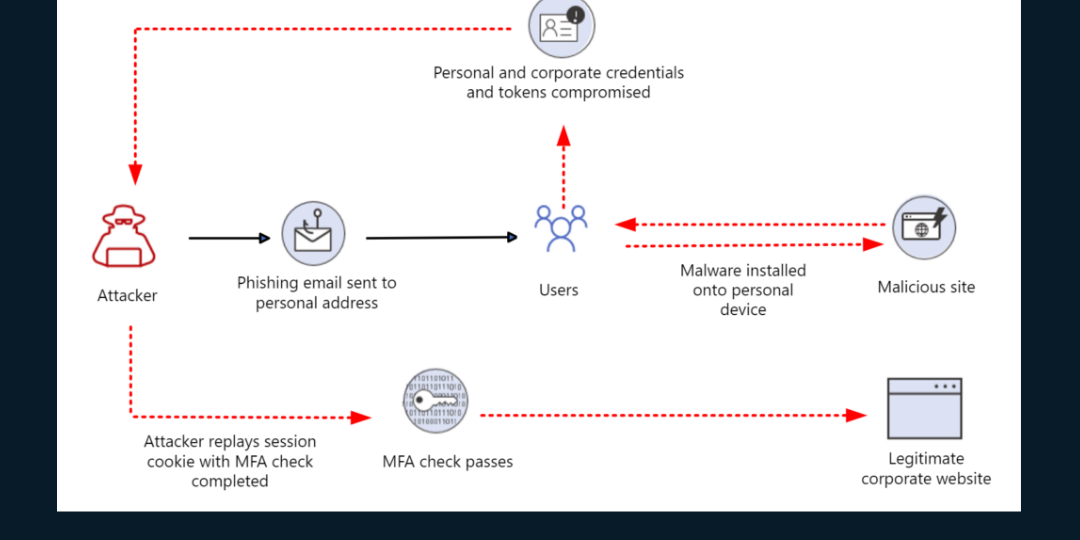
Cloud Token Theft is an attack technique in which an adversary steals authentication tokens that have already been legitimately issued by a cloud identity provider—such as Microsoft Entra ID—and reuses them to access protected resources without triggering a new authentication process.
From the system’s perspective, the attacker is not an attacker at all. They are simply presenting valid proof of authentication.
This makes Cloud Token Theft fundamentally different from traditional attacks:
| Traditional Identity Attacks | Cloud Token Theft |
|---|---|
| Steal credentials | Steal sessions |
| Attack authentication | Abuse authorization |
| MFA is a barrier | MFA already completed |
| Login-based detection | Session-based stealth |
In modern cloud environments, identity is no longer bound to a person—it is bound to a token.
Understanding Tokens in Modern Authentication
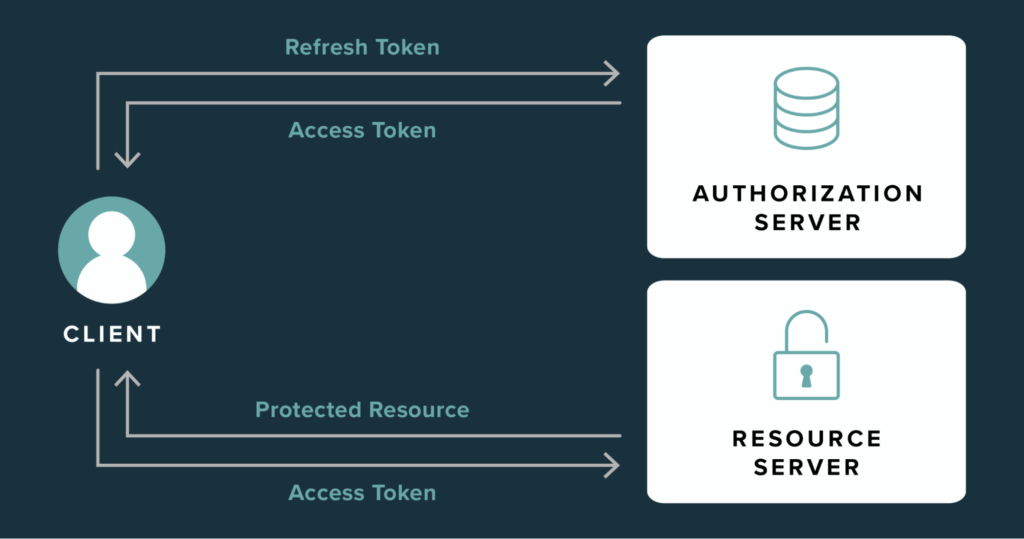
Cloud authentication relies on standards such as OAuth 2.0 and OpenID Connect. While implementations vary, the underlying logic is consistent:
- The user successfully authenticates (password + MFA)
- The identity provider issues:
- Access Tokens – short-lived tokens used to access APIs and services
- Refresh Tokens – longer-lived tokens used to obtain new access tokens
- Session Cookies – browser-based persistence mechanisms
- Applications trust the token, not the user
This model offers efficiency and scalability, but it also introduces a critical security implication:
Possession of a valid token is equivalent to being the user.
Once issued, a token is typically accepted without re-evaluating how, where, or by whom it is being used—unless additional controls are explicitly enforced.
Why Cloud Token Theft Is So Dangerous
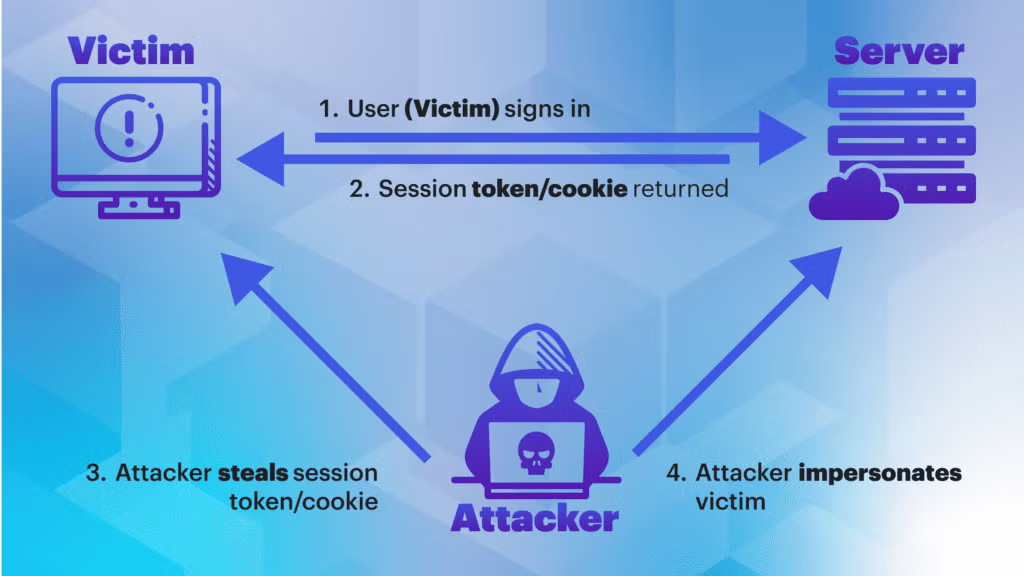
1. MFA Is Not Broken—It Is Circumvented
MFA works exactly as designed. The user completes a strong authentication process, and the system issues tokens accordingly. The attacker operates after this point, abusing the outcome of MFA rather than defeating it.
This distinction is critical: organizations often assume MFA equals safety. Cloud Token Theft demonstrates that MFA alone protects authentication, not ongoing access.
2. Conditional Access Is Often One-Time Evaluation
Many Conditional Access policies are enforced:
- At login
- At token issuance
- During interactive authentication
Once a token is issued, it may remain valid even if:
- The user’s risk level changes
- The IP address changes
- The device context changes
Without continuous evaluation, tokens become long-lived trust artifacts.
3. High Persistence, Low Visibility
Refresh tokens can allow attackers to maintain access for extended periods. During this time:
- No new login events occur
- No MFA challenges are triggered
- Activity appears legitimate
Security teams may only notice anomalies after significant damage has occurred.
Token Theft Happens at the Endpoint
Cloud Token Theft does not exploit weaknesses in the identity provider itself. Instead, it targets the user endpoint, where tokens must exist in memory, storage, or browser context.
Common theoretical vectors include:
- Infostealer malware
- Malicious browser extensions
- Compromised user profiles
- Memory scraping techniques
- Persistent session cookies
- Local session fixation
This highlights a crucial reality:
Cloud identity security is inseparable from endpoint security.
A fully hardened cloud environment can still fall if endpoints are compromised.
Enterprise Impact of a Successful Attack
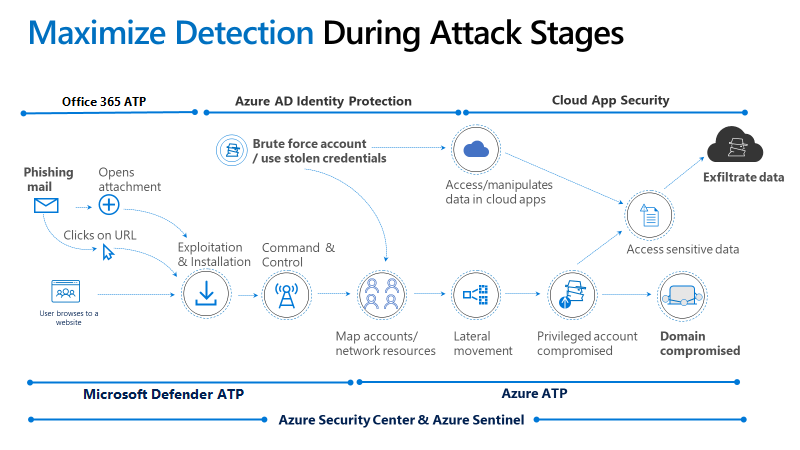
When Cloud Token Theft succeeds, attackers may gain access to:
- Corporate email and calendars
- SharePoint and OneDrive repositories
- Collaboration platforms such as Teams
- Cloud APIs and internal services
- Sensitive business and customer data
Because access is authenticated, attackers can:
- Move laterally across cloud services
- Exfiltrate data slowly and quietly
- Blend into normal user behavior
- Establish long-term persistence
This makes Cloud Token Theft particularly dangerous in regulated industries and high-value targets.
The Limitations of MFA in Token-Based Systems
MFA is a necessary control, but it is not sufficient on its own.
| Security Control | Effectiveness |
|---|---|
| Password + MFA | ❌ Partial |
| Push / OTP MFA | ❌ Ineffective post-auth |
| Phishing-resistant MFA | ⚠️ Improved |
| Device-bound tokens | ✅ Critical |
| Continuous evaluation | ✅ Essential |
Cloud Token Theft exposes the gap between authentication security and session security.
Conceptual Indicators of Compromise
Although stealthy, Cloud Token Theft can produce subtle signals, such as:
- Activity without recent authentication events
- Access from inconsistent geolocations
- API usage without user interaction
- Behavioral deviations over time
- Session durations exceeding normal baselines
Detecting these signals requires behavioral analytics and correlation, not static rules.
Modern Defensive Strategies: A Zero Trust Perspective
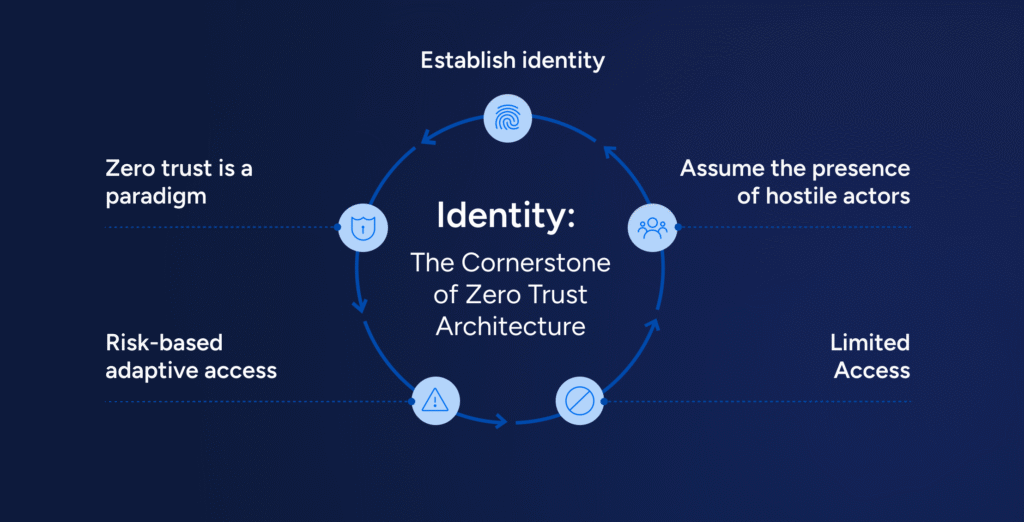
Defending against Cloud Token Theft requires a shift in mindset:
- Treat tokens as revocable, not trusted
- Reduce token lifetimes wherever possible
- Enforce Continuous Access Evaluation
- Bind sessions to device posture and identity
- Monitor behavior throughout the session
- Integrate endpoint and identity telemetry
Zero Trust is not about denying access—it is about constantly re-evaluating trust.
Conclusion
Cloud Token Theft is not a theoretical curiosity—it is an inevitable outcome of token-based identity systems when trust is granted once and rarely re-evaluated.
Organizations that rely solely on MFA are securing the front door, while leaving sessions and tokens exposed.
Understanding this attack is essential for any security team aiming to design resilient, modern identity architectures aligned with real Zero Trust principles.