Attack methods: Cross-origin resource sharing (CORS)
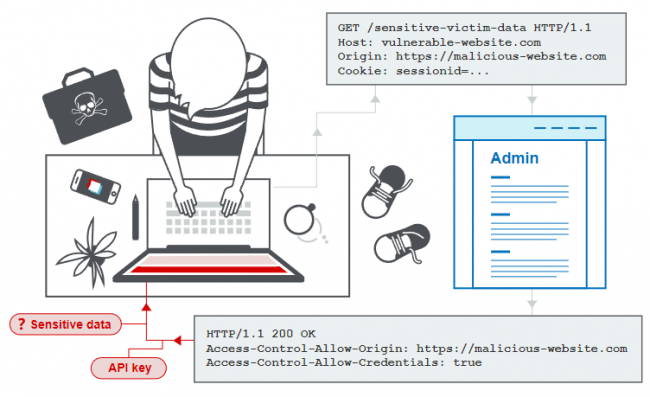
In this section, we will explain what Cross-Origin Resource Sharing (CORS) is, describe some common examples of attacks based on Cross-Origin Resource Sharing, and discuss how to protect against these attacks. Requirements: Responsibility: In this tutorial, we will use hacking techniques for educational purposes only. We do not promote their use for profit or improper…