Advanced Kerberos abuse using Restricted Delegation and Protocol Transition (S4U)
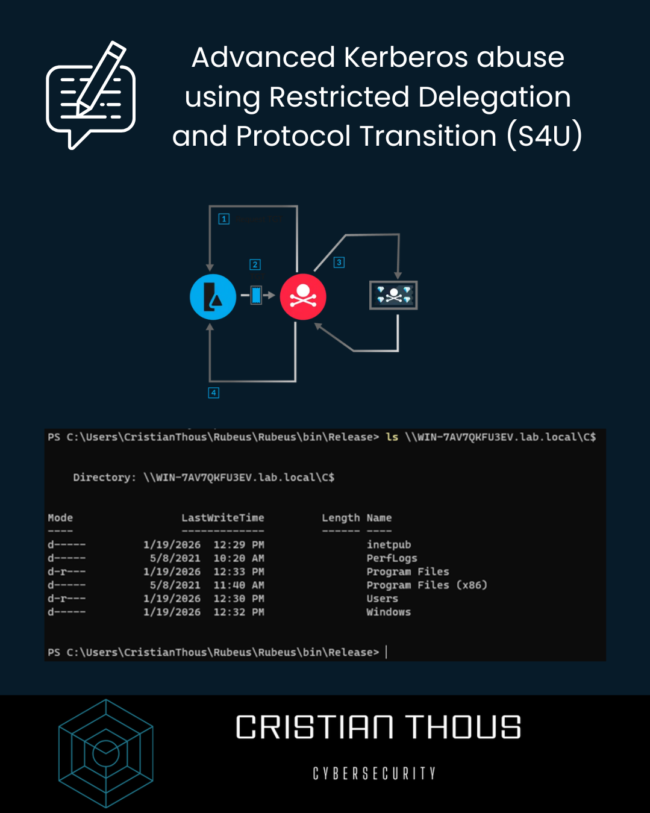
Kerberos is one of the most robust authentication protocols ever designed for enterprise environments. Its strength, however, does not rely solely on cryptography, but on a strict trust model enforced by the Key Distribution Center (KDC). When that trust model is misdesigned or poorly maintained, Kerberos can become a powerful attack vector capable of leading…