A script to remotely dump files and folders from a Windows SMB share
Requirements:
- Windows system – A Windows system to perform the tests
- Programming – Advanced programming skills
Responsibility:
In this tutorial, we will use hacking techniques for educational purposes only. We do not promote their use for profit or improper purposes. We are not responsible for any damage or impairment that may be caused to the systems used. The user of this tutorial is solely responsible.
Knowledge:
- Linux – High
- Programming – Medium
- Kali Linux – High
- Windows – Very high
- Networking – Low
Overall tutorial level: High
Ideal for: Systems engineers, security engineers, pentesters
What is an SMBShare dump?
First, we must understand what SMB is
The Server Message Block (SMB) protocol is a network file sharing protocol that allows applications on a computer to read and write files and request services from programs on a server in a computer network. The SMB protocol can be used over the TCP/IP protocol or other network protocols. Using an SMB protocol, an application (or an application user) can access files or other resources on a remote server. This allows applications to read, create, and update files on a remote server. SMB can also communicate with any server program that is configured to receive a request from an SMB client. SMB is a fabric protocol used by software-defined data center (SDDC) technologies, such as Direct Storage Spaces and Storage Replication.
If you want to know more, here is a complete tutorial: SMB: What is it and how does it work?
Let’s get started
First, we must download the content from this link DumpSMBShare
Here is an explanation of all the possible commands and methods of use:
Directory to search (default: /)
–debug Enables debug output. (Default: False)
-q, –quiet Enable DEBUG output authentication: -H LMHASH:NTHASH,
–hashes LMHASH:NTHASH NTLM hashes,
the format is LMHASH:NTHASH –no-pass Do not ask for password (useful for -k) -k,
–kerberos Use Kerberos authentication.
Takes credentials from ccache file (KRB5CCNAME) based on target parameters.
If no valid credentials are found, it will use those specified on the command line -A hexadecimal key,
–aesKey hexadecimal key AES key to use for Kerberos authentication (128 or 256 bits) connection: –dc-ip ip address IP address of the domain controller.
If omitted, the domain part (FQDN) specified in the target parameter will be used. -I ip address,
–target-ip ip address IP address of the target machine.
If omitted, whatever is specified as the target will be used. This is useful when the target is the NetBIOS name and cannot be resolved. -P [destination port],
–port [destination port] Destination port to connect to the SMB server.
The first step is to run the script.
./SumpSMBShare.py 'LAB.local/user2:Admin123!@192.168.2.1' -share 'SYSVOL' -debug
This will give us the following result:
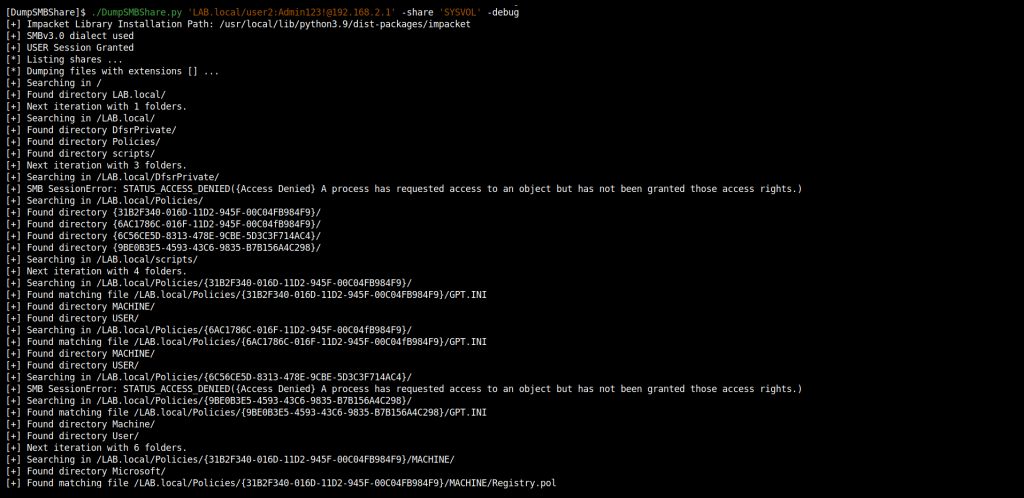
Here are the results.
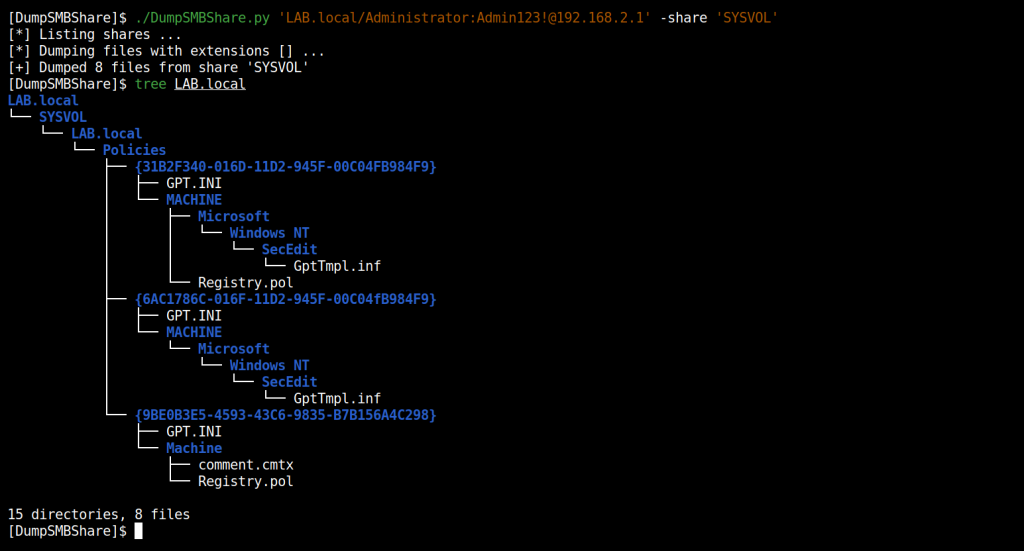
I hope this is helpful.